Security
AI and Cybersecurity: Innovation Trends Evolve with Threats
Key Points
- The increasing sophistication of cyber threats poses challenges for individuals and organizations, but it is also driving opportunities for innovation in cybersecurity.
- Specifically, AI/ML-based security and compliance frameworks, such as large language models (LLM) and generative AI, continue to be hot topics after dominating the agenda at RSA Conference 2024.
- A technology brief from CableLabs details more takeaways from the conference, including generative AI-based automation and its impact on SBOM, crypto-agility and zero trust.
We are witnessing a transformation in the security landscape across all aspects of our digital world. As cyber threats become increasingly sophisticated and frequent, they pose new challenges for individuals and organizations alike. A single security breach can have crippling consequences for potentially millions of internet users — from the disruption of daily life and loss of access to everyday services to identity theft and loss of privacy.
A silver lining, though, is that these threats are driving a wave of cutting-edge innovations and solutions that can help safeguard our sensitive data and ensure continuity of operations. At the forefront of this evolution are artificial intelligence and machine learning (AI/ML). These technologies are equipping cybersecurity professionals with tools to identify and mitigate threats more effectively than ever before with unprecedented speed and accuracy.
It’s no surprise that the proliferation of AI/ML has become a central focus at industry conferences and among cybersecurity professionals. This was evident at this year’s RSA Conference, where tracks focused on automation using AI/ML, as well as the benefits and threats due to generative AI and large language models (LLMs).
Other key topics included increased usage of software bills of materials (SBOMs) and security threats associated with it, and zero-trust sessions focused on policy-based authentication. In case you missed it, CableLabs covers these topics and provides more detailed key findings from the RSA Conference 2024 in a recent tech brief, available exclusively to members. Below are a few general observations from the conference.
A Double-Edged Sword
Generative AI and LLM came up in summits hosted by organizations including the Cloud Security Alliance (CSA), the Open Worldwide Application Security Project (OWASP) and the Techstrong Group. Among the topics were:
- The use of LLM and generative AI to accelerate code analysis and patch code vulnerabilities, speed up incident responses, detect multimodal malware as well as improvements in threat detection, continuous vulnerability and risk management for organizations.
- Demonstrations of LLM attacks that can produce outputs that are entirely or partially incorrect and/or harmful. Common attacks presented in various sessions included prompt injection, insecure output handling, poisoning of training data, denial of service on the LLM, exfiltration, etc.
The OWASP Foundation provided a summary of their work on the “Top 10 for LLM” project that addresses common LLM security risks and provides guidance and checklists when implementing and managing LLMs.
There are also several policy-related challenges of generative AI like copyright protection of AI-generated work and tracing back the training data to the original owners, lack of recommendations or regulations from the United States Patent and Trademark Office regarding AI and human inventorship and also around privacy of personal data shared with generative AI vendors with the risk of such data being reidentified by the AI tools.
Long Live Shorter Certificates
An ongoing trend in the public key infrastructure (PKI) world is the shortening of the lifespan of operational certificates. Specifically for web and cloud infrastructure environments, Google published a roadmap that limits the TLS certificates’ validity period from 398 days to 90 days. The primary benefits touted for shorter validity certificates include reduced exploitation time of compromised certificates and crypto-agility, collectively termed as certificate agility.
However, this also poses challenges for access network operators and certificates meant for device identities whose validity period can extend into decades. Typically, the purpose of such device certificates is to provide immutability, attestability and uniqueness and, they are primarily used for access network authentication. In this context, providing a consistent identity using rotating certificates necessitates a change from existing deployment models. It highlights the need for implementing automated certificate management tools and incorporates the additional costs and time to deploy it as part of the network infrastructure upgrade.
Software and Cryptographic Bills of Materials
SBOMs are gaining traction as one of the key ingredients of the software development lifecycle. The RSA Conference also included some interesting sessions and demonstrations of adversarial use of SBOMs and developing guidance on how to correctly use them.
From the security perspective, cryptographic bills of materials (CBOMs) provide a mechanism to track cryptographic assets and their dependencies. It also provides a path toward introducing and tracking quantum-safe solutions by making it easier to track deprecated ciphers. This is one area with rapid development and many vendors demonstrating SBOM tools and SBOM best practices.
Other Hot Topics
Other notable technologies and topics covered at the conference included:
- Zero Trust and Identity Protection — Identity compromise continues to be a top threat and the root cause of data breaches. With the current trends around remote work, virtualization and cloud deployments, data and identities are now stored outside of corporate perimeters. Incorporating a zero-trust model (never trust, always verify) plays a crucial role in protecting identity and corporate assets.
- Multi-Factor Authentication — More and more companies are moving towards MFA to reduce account compromises. However, different attack methods to bypass MFA — like MFA fatigue, SIM swapping and session hijacking — complicate this.
- Post Quantum Cryptography (PQC) — The discussion around PQC continues with the general guidance that the industry incorporate a “hybrid mode” of deployment for any new cryptographic solutions. As of August 2024, there is not yet a stable quantum computer capable of widespread practical use; however, cybercriminals continue to steal encrypted data with the expectation of decrypting it in the future. NIST plans to publish the first set of PQC standards by the end of this summer.
The RSA Conference is the flagship conference for cybersecurity experts. This year it brought together 41,000+ professionals, 650 speakers across 425 sessions and over 600 exhibitors in San Francisco. Read more about these cybersecurity trends and more RSA Conference topics in the tech brief, available exclusively to CableLabs member operators.
Did you know?
In addition to in-depth tech briefs covering events like the RSA Conference, CableLabs publishes short event recap reports — written by our technologists, exclusively for our members. Catch up on recent recaps (member login required).
Security
Cybersecurity Awareness Month and Beyond: How We’re Safeguarding Network Integrity
In the digital age, cybersecurity is the first line of defense against an ever-expanding and continually evolving array of threats. The increasing sophistication of cyber threats and a deepening dependence on interconnectivity have elevated cybersecurity technologies from a peripheral consideration to a critical priority.
October is Cybersecurity Awareness Month, but safeguarding digital integrity is a year-round commitment for CableLabs. In our Security Lab, we work to identify and mitigate threats to the access network. We proactively develop innovative technologies that make it easier for internet users to protect their digital lives.
Let’s take a look at some of the CableLabs technologies that are enhancing network security and reshaping the way we protect ourselves online.
DOCSIS 4.0 Security
The new DOCSIS® 4.0 protocol is another promising chapter in the successful life of hybrid fiber coax (HFC) networks, and it brings with it notable security enhancements to the broadband community.
It’s important to note that DOCSIS 4.0 cable modems (CMs) are compatible with existing DOCSIS 3.1 networks. This allows the CMs to take advantage of higher speed tiers even without needing to upgrade the network at the same time. To fully leverage the new upstream bandwidth efficiency and security features of the protocol, both modems and cable modem termination systems (CMTSs) need to support DOCSIS 4.0 technology.
Another key security-enhancing element of the technology is that DOCSIS 4.0 networks come with upgradable security. The technology continues to support the Baseline Privacy protocol (BPI+ V1) used in DOCSIS 3.1 specifications. It also integrates the new version that can be enabled as needed (BPI+ V2).
The new version introduces mutual authentication between devices and the network, eliminates the dependency on the Rivest Shamir Adleman (RSA) algorithm and implements modern key exchange mechanisms. This change enhances device authentications with Perfect Forward Secrecy and cryptographic agility and aligns DOCSIS key exchange mechanisms with the latest Transport Layer Security (TLS) protocol, v1.3.
Further upgrades include enhanced revocation-checking capabilities with support for both Online Certificate Status Protocol (OCSP) and Certificate Revocation List (CRL) in DOCSIS 4.0 certificates. DOCSIS 4.0 also introduces standardized interfaces for managing edge device access (SSH) aimed at limiting the exposure of corporate secrets (e.g., technicians’ passwords) and incorporates a Trust on First Use (TOFU) approach for downgrade protection across BPI+ versions.
Ultimately, the new DOCSIS 4.0 security is designed to provide several options for network risk management. These features include new speeds and capabilities that can be utilized alongside today’s security properties and procedures (e.g., BPI+V1 with DOCSIS 3.1 or DOCSIS 4.0 CMTSs) and advanced protections when needed.
Matter Device Onboarding
Passwords are meant to be secret, so why are users sharing them with all of their Internet of Things (IoT) devices? At CableLabs, we’re working to make it easy for end-users to add devices to their home networks without needing to share a password with every device.
Because so many devices are communicating with one another, standardization is critical — especially when it comes to security. That’s where Matter comes in. The open-source connectivity standard is designed to enable seamless and secure connectivity among the devices in users’ smart home platforms.
Our vision is for each device to have its own credential to get on the Wi-Fi network. The access point (AP) would use this unique credential to grant the device access to the network, and the device then would verify the AP’s credential. This has three incredibly significant advantages for subscribers:
1. It vastly increases the security of the home network. This is because a compromised device cannot divulge a global network password and lead to a compromise of the entire network.
2. It’s possible to leverage the device attestation certificate that comes with every Matter device to inform the network that it’s a verified and certified device.
3. There's no need to reset every single device on the network if the Wi-Fi password is changed.
Join us for a demonstration of Matter at SCTE® Cable-Tec Expo®, which is October 17–19 in Denver, Colorado. Come see us in CableLabs’ booth 2201 to see the future of networked IoT devices and how scanning a QR code can get a device on a network with its own unique credential.
CableLabs Custom Connectivity for MDUs
One of the fastest-growing market segments for broadband providers worldwide is the multi-dwelling unit (MDU) segment. The opportunities here include fast-growing apartment communities, as well as segments such as emergency/temporary housing, low-cost housing, the hospitality and short-term rental markets, and even emergency services.
A common theme across these is the need for an alternate deployment model that allows on-demand service activation and life-cycle management, as well as custom connectivity to various devices. The traditional deployment model of installing customer premises equipment (CPE) on a per-subscriber and/or per-unit basis has hindered operators in delivering services to these segments in a cost-effective manner.
The CableLabs Custom Connectivity architecture is designed to address these constraints by providing dynamic, on-demand subscription activation and device-level management to consumers across the operator’s footprint — without the need to deploy a CPE. The architecture leverages the security controls and mechanisms designed within the CableLabs Micronets technology to provide dynamic, micro-segmentation-based subscription delivery where a subscriber’s devices can connect to their “home subscription” from anywhere on the network and across different access technologies (Wi-Fi, cellular, etc.).
Additionally, it provides consistent operational interfaces for device authentication and service provisioning, as well as billing and subscription management interfaces to enable on-the-fly subscription activation and management.
Safer Networks, Empowered Users
The importance of proactive cybersecurity measures can’t be overstated, and these cutting-edge technologies are proof of CableLabs’ ongoing commitment to enhancing network security. These innovations not only make our networks safer, but they also empower users to take charge of their own online security.
By staying at the forefront of cybersecurity advancements, CableLabs continues to ensure we can all navigate the digital world with greater confidence and peace of mind.

Security
Raising the Bar on Gateway Device Security

Today, CableLabs® has publicly released a set of best common practices (BCP) to enhance the security of cable modems, integrated access points, and home routers (collectively, known as “gateway devices”) against malicious activity and other cyber threats. This work builds on and extends CableLabs’ and the cable industry’s longstanding leadership in cybersecurity to ensure a consistent and robust baseline for gateway device security, increased economies of scale, and an ontology for simplified communication and procurement between network operators and device manufacturers.
The BCP Working Group is comprised of security technologists from CableLabs, network operators from around the world, and gateway device manufactures, including representatives from CableOne, Charter, Cisco, Cogeco, Comcast, Commscope, Cox, Liberty Global, MaxLinear, MediaCom, Shaw and Technicolor. In developing the BCP, the Working Group drew heavily upon well-established and widely accepted security controls, recognized broadly by industry and government security experts.
The cable industry has long employed extensive network security practices to ensure the confidentiality, integrity and availability of broadband services, including gateway devices. The BCP expands and standardizes these network security practices for gateway devices and complements cable operators’ broader set of security practices. For instance, DOCSIS® Security testing is performed on all gateway devices to ensure DOCSIS protocol conformance, including the verification of the correct implementation of public key infrastructure (PKI) authentication and identity management, BPI+ encryption, and EAE (Early Authentication and Encryption) secure provisioning requirements.
The BCP document goes beyond DOCSIS Security requirements and provides a framework for the full range of security considerations applicable to gateway devices, including hardware and manufacturing considerations, default security settings, configuration procedures, secure boot, roots of trust, software/firmware development and verification, encryption requirements for both data in transit and data at rest, and physical security, among others. To further ensure the robustness of the BCP, the working group compared and mapped the BCP to NIST’s general guidance for connected devices used by the federal government, to help confirm the scope was fully comprehensive of applicable security considerations.
The BCP represents the industry coalescing around a common set of security baseline requirements that furthers the following critical goals:
- Provide a common framework for security elements and controls within gateway devices, including cable modems, integrated Wi-Fi access points, and home routers, to align the varied approaches to device security across the industry.
- Create a community of manufacturers and network operators collaborating to enhance gateway device security.
- Leverage well-established and well-vetted security controls and practices to minimize the risk of unknowingly introduced vulnerabilities or other security weaknesses.
- Harmonize security requirements across network operators to drive increased economies of scale, lowering the cost of broadband deployment.
- Further protect network resources and broadband service from malicious attacks.
- Provide a framework for network operator assurance that enables verification of testable practices and configurations.
- Enable alignment across standards, regulatory, and compliance regimes through a transparent and open set of best common practices.
- Establish a security framework for gateway devices that builds in flexibility and agility, so that manufacturers and network operators can address and adapt to new threats and changes in the cyber risk landscape.
While this initial release is an important achievement, one that strives to be comprehensive in terms of security posture for gateway devices, we all recognize that this field is constantly evolving and advancing. We see the BCP as a framework that must and will be updated and maintained as network technology, device security, and unfortunately, adversary techniques continue to evolve. To that end, we invite and welcome additional gateway and modem manufacturers as well as additional network operators to join the working group as we continue to progress this effort.
On October 13, 2021, at 3:00 pm ET, we invite you to join our virtual panel session at SCTE Cable-Tec Expo to discuss and further explore Gateway Device Security and our work to develop the BCP.

Security
CableLabs® Micronets Security Reference Code Is Now Open Source

In November, we introduced CableLabs micronets, a next-generation on-premise networking platform focused on providing adaptive security for all devices connecting to home or small business networks. Micronets uses dynamic micro-segmentation to manage the connectivity to each device and is designed to provide seamless and transparent security without burdening end users with the technical aspects of configuring and maintaining the network. Micronets is also a foundational piece of the cable industry’s recently announced 10G vision – supporting increased security for home and small business users.
Today we are pleased to announce that the release of the micronets reference implementation as open source software. You’ll find links to files and details on how to build and deploy the different Micronets components here. CableLabs plans to continue to develop and add new features to the open source reference implementation – we also welcome contributions from the broader open source community.
Why Open Source?
Here at CableLabs, we believe in the importance of sharing our code to accelerate the adoption of new ideas and to stimulate industry-wide innovation. In this particular case, there was an even stronger sense of urgency to do so.
The rapid and growing proliferation of Internet-connected devices, or the “Internet of Things” (IoT), has ushered in a new era of connectivity that gives us unprecedented control over our environment at home and at work. Unfortunately, along with all the benefits comes significant risk to end users and the broader Internet, alike. Vulnerable IoT devices are the fuel for botnets and other distributed threats. Compromised IoT devices are used to launch distributed denial of service (DDoS) attacks, spread ransomware, send spam, and more generally, enabling the theft of personal or sensitive information. Moreover, vulnerable IoT devices may also create the risk of physical harm, as many connected devices now provide a bridge between the cyber and physical worlds.
CableLabs and the broader IoT ecosystem are committed to driving improved IoT security, but such efforts are not enough alone to address the risks of insecure IoT. We must also develop network technologies, such as micronets, to help mitigate the risks of insecure IoT. There will always be legacy devices that don’t meet current IoT security best practices and potentially, manufactures that don’t follow best practices.
We believe addressing the risks of insecure IoT is a shared responsibility. By releasing the reference code as open source, we’re hoping to accelerate the adoption of micronets and encourage others to build upon our work.
More on Micronets and How it Fits into Our Security Agenda
The micronets platform leverages advanced mechanisms like device fingerprinting and artificial intelligence to enable real-time detection and quarantining of compromised IoT devices, minimizing the risk to other devices on the local network and to the broader Internet. Micronets can also provide enhanced security for high-value or sensitive devices, further reducing the risk of compromise for these devices and applications. Despite the complex technology under the hood, this self-organizing system is geared toward an everyday consumer and is very easy to use. For a deeper dive into micronets’ security features, please download the micronets whitepaper here. Missed our recent public webinar? You can find it on youtube here.
Micronets is just one of many active security projects at CableLabs. For instance, we’re also working on advancing additional cyber-attack mitigation technologies, such as DDoS information sharing, IP-address spoofing prevention and more, as well as actively contributing to industry and government efforts to drive increased IoT security. And although there’s no single solution that protects every network, we will continue working with our members and vendors and various industry organizations to develop better tools that make our world a safer place—one network at a time.
Click below for details on how to build and deploy the different Micronets components.

Security
Micronets: Enterprise-Level Security Is No Longer Just For Enterprises

Today we are introducing CableLabs® Micronets, a framework that simplifies and helps secure increasingly complex home and small business networks.
As we add devices to our networks such as cell phones, computers, printers, thermostats, appliances, lights and even medical monitors, our networks become more susceptible to intrusions. Micronets automatically segments devices into separate, policy-driven trust domains to help protect the devices, data and the user. Agile and easy-to-use, Micronets gives consumers increased protection and control of their local network without overwhelming them with technical details. Micronets reduces the risks associated with vulnerable devices but is not a substitute for strong device security.
The Micronets Advantage: Smart Security and Ease of Use
CableLabs Micronets is an advanced network management framework that utilizes three components to provide enhanced security:
Automated Networked Devices: While CableLabs is not the first organization to introduce the concept of network segmentation, Micronets’ primary advantage is in its implementation. The Micronets framework uses advanced mechanisms like device fingerprinting and Manufacture Usage Definitions (MUD) to intelligently group networked devices into dynamically managed trust domains or “micronets.”
For example, children’s devices are assigned to one micronet, home automation on another and so on. If one device is compromised, devices on the other micronets will not be visible to the attacker. The system will automatically quarantine the infected device, minimizing the risk to the network and other connected devices. While the system is largely autonomous, the user has the visibility and control to adjust trust domains and add new devices.
Seamless User Experience: Micronets provides a layer of dynamic management and secure credential provisioning that hides the complexity associated with network orchestration and focuses on improving the user experience. It’s a self-organizing platform that’s very easy to use and control which is a major benefit to an average customer who lacks the time and knowledge required for manual network administration.
Adaptive Devices: The Micronets framework also includes an intelligence layer that manages the connectivity between the individual trust domains, the Internet and third-party provider services. Because security threats continuously evolve, Micronets is built to evolve as well. State-of-the-art identity management and cloud-based intelligence technologies, like machine learning and neural networks, are leveraged to provide adaptive security that can evolve over the years, thereby providing a solution that will work for today’s as well as tomorrow’s needs.
Another benefit that Micronets can provide is enhanced security for highly sensitive devices or applications, through secure network extension via APIs. For example, Micronets can be used to establish a secure, end-to-end network connection between an Internet-connected medical device, like a glucose tester, and the cloud services of a healthcare provider. This enhanced capability provides confidentiality, integrity and availability of the medical device and the healthcare data to and from the device.
Micronets provides features, such as network isolation, similar to 5G network slicing but can operate across Wi-Fi and mobile networks. Micronets is focused on security of private networks (e.g., home networks and SMB networks) where 5G slicing is focused on different service segment performance levels of end to end networks. Since Micronets is an overlay technology, it’s compatible with existing networks, even 5G slicing, where 5G slicing is dependent on the broad deployment of the underlying 5G technologies.
Under the Hood: A Deeper Dive into How Micronets Works
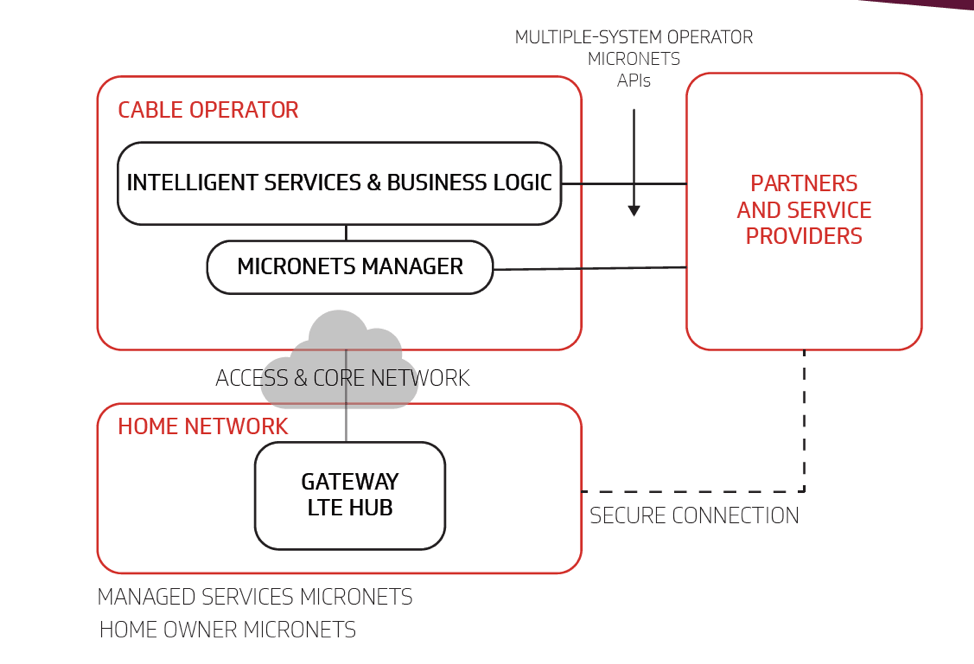
Micronets has five major architectural components:
- Intelligent Services and Business Logic: This layer acts as the interface for the Micronets platform to interact with the rest of the world. It functions as a receiver of the user’s intent and business rules from the user’s services and combines them into operational decisions that are handed over to the Micronets Manager for execution.
- Micronets Manager: This critical element orchestrates all Micronets activities, especially flow switching rules between the home network, cable operator and third-party providers that allow the delivery of services. It also provides controls that allow the user to interact with the Micronets platform.
- Micronets Gateway: Micronets Gateway could be a cable modem, router, wireless access point, or LTE hub/femtocell. It’s a core networking component that uses Software Defined Networking (SDN) to define how Micronets services interact with the home network. It also oversees the entire device profile on the user network—both wired and wireless.
- The Home Network: All the devices on the customer’s home or SMB network are automatically organized into appropriate trust domains—or micronets—using the device identity and SDN based logic. However, the customer can always make manual changes through a user-friendly Micronets interface.
- Micronets API: Operator partners and third-party operators can interact with the Micronet manager via secure APIs. Micronets ensure that third-party devices and services are secured through mutual authenticated and encrypted communications channels.
The Rollout: Getting Micronets In Homes and Business
- White Paper: Our white paper lays out the vision and architecture of Micronets in greater detail.
- Industry Partnerships: We’re working with our industry partners and cable operator members to bring Micronets to consumers. We are also working on implementing an easy-onboarding framework that builds on top of features from the Wi-Fi Alliance (WFA), namely EasyConnect, WPA3 security and the Internet Engineering Task Force (IETF) Manufacturer Usage Description framework to enable the secure and seamless configuration and on-boarding of consumer devices. We are also leading the development of a secure interoperability specification for IoT devices in the Open Connectivity Foundation, and with Micronets, we’re making significant strides to simplifying and securing increasingly complex networks.
- Code: We are releasing the reference code, currently under development, to the open source community in the coming months.
- Government Collaboration: We’re participating in and supporting government efforts like NIST’s National Cybersecurity Center of Excellence project on mitigating botnets in home and small business networks.
- Our Members and Vendors: We are planning on developing and publishing specifications for standardized API’s for advanced security services based on machine learning and device fingerprinting in collaboration with our members and vendors.
CableLabs has long been a leader in the development of security technologies for the delivery of video and broadband Internet access services. With Micronets we are bringing our expertise to the growing world of connected devices, for which security is a shared responsibility across the Internet ecosystem. Micronets helps mitigate the risks associated with insecure IoT, but is not a substitute for or alternative to the ongoing efforts to drive increased device security, to prevent vulnerabilities at their source.
Download our white paper by clicking below or learn more here.
Interested in working with the CableLabs team or hearing more about Micronets? Contact Darshak Thakore (d.thakore@cablelabs.com).
Consumer
Where is that Set-top Box?

As a technology developer in the cable industry, my friends often ask me questions like, "Why do I need all these boxes in front of my TV?", "Why do I need to use so many remotes?" , and "When will I be able to watch TV on my mobile/tablet?" My enthusiastic response has been, "Very soon!” And then I explain the Digital Living Network Alliance's CVP-2 Guidelines, and how this new technology leverages the latest HTML5 web standards to allow consumers to view their TV content on any device of their choice. The responses I receive range from the optimistic "Great! How Soon?" to the skeptical "I'll believe it when I see it", which is why I was really excited when DLNA launched the VidiPath Certification Program.
VidiPath enables TV services to be viewed on various devices like tablets, phones, Smart TVs, and game consoles within the consumer's home. More details about CVP-2 are available as a previous post to this blog. However, the relationship between CVP-2 and the VidiPath Certification deserves some explanation. CVP-2 was geek-speak for the technology guidelines while they were being developed in the industry. Now completed, the VidiPath™ brand has been born.
Ok, back to my excitement about the VidiPath Certification Program. The reasons are twofold. First and foremost, the certification launch means that the industry is just one final step from getting the CVP-2 technology into the market and in consumers’ homes. The other reason is that the CableLabs CVP-2 Server was qualified by DLNA as a CVP-2 Reference Server and selected for use in the VidiPath Certification Testbed.
Benefits of VidiPath to Consumers
VidiPath will allow a consumer to watch premium TV content on any VidiPath certified device within their home, and that is just the tip of the iceberg. Consumers will also be able to enjoy the following benefits with their VidiPath devices:
- Putting aside that extra remote to navigate and watch content.
- No longer needing multi-room set-top boxes.
- Watching TV on tablets or mobile phones while everyone else is watching something else on the big TV.
- Gaining a modern yet consistent user interface on all devices to navigate and bookmark content.
- Reclaiming entertainment center real estate by moving the set-top box to the basement or a closet.
CableLabs CVP-2 Reference Server (or How Has CableLabs Contributed?)
To support the success of VidiPath, CableLabs has been actively involved in the development of the CVP-2 guidelines and has also developed a CVP-2 Server utilizing a number of existing open source components to accelerate the development and adoption of VidiPath in the industry. To that effect, we had: a) good success right from the start with the Intel OTC team contributing code to Rygel, b) various companies utilizing our code base for their testing/development and providing us feedback, and c) our collaboration with Elliptic Technologies and utilizing their robust tVault for DTCP-IP solution in the CableLabs Reference Server to provide content protection and authentication. We are already shipping out the Reference Server to various DLNA members who are preparing to get their clients certified. Now we look forward to VidiPath clients getting certified and hitting the market.
In addition, CableLabs holds CVP-2 interoperability events (interops) about twice a year. During these interops, manufacturers and cable operators come together to evaluate how their client or server interacts with other CVP-2 clients and servers. We just finished up another successful interop, with sixteen different companies participating.
And finally, CableLabs has a VidiPath Interoperability Lab, where VidiPath client developers can develop and test against MSO VidiPath guides, as well as work with the CableLabs CVP-2 Reference Server and other DLNA CVP-2 test tools.
Contact info: Darshak Thakore is a Lead Architect in the Applications Technologies Group at CableLabs.




