Security
Addressing Emerging Cryptographic Threats in the Age of Quantum Computing

Key Points
- Threats against cryptography are evolving; among them, the threat of quantum computing is increasingly putting critical infrastructure and the data that traverses it at risk.
- Enabling cryptographic agility and leveraging it to migrate to quantum-safe cryptography are approaches that can mitigate these emerging threats.
- Through CableLabs’ Future of Cryptography Working Group, we collaborate with operators and vendors to help the industry navigate the migration to new cryptographic paradigms.
Cryptography is a foundational security technology used to protect digital information by providing the underpinnings for confidentiality, authentication and integrity. Today’s cryptographic algorithms may soon be undermined by emerging attacks, including the realization of a cryptographically relevant quantum computer (CRQC). Such attacks pose a very real and increasingly urgent threat across virtually all industries and their technologies, including broadband network infrastructure.
With cryptography and public key infrastructure being foundational to the security of cable networks, the broadband industry is uniquely positioned to rise to this challenge and seize the opportunity to future-proof networks to be robust, flexible and responsive to any cryptographic threat — quantum or otherwise. In this blog, we’ll review the threats against cryptography on the horizon, the solution to mitigate those threats and actions to start migration to new cryptographic paradigms. Many organizations, including network operators, have started taking action to plan for and execute cryptographic migrations.
The Threat: Attacks Against Cryptography
So, what exactly is the risk? To put it simply, quantum computers will one day be powerful enough to crack the asymmetric cryptography that is the basis of confidentiality, authenticity and integrity of data at all layers for virtually all devices deployed today. The current timeline for the potential development of a CRQC is 10–30 years — with increasing probability. That estimate isn’t certain, and recent research advancements suggest that it could be sooner.
While that time frame is wide, the risk of compromise is relevant today, thanks to the “harvest now, decrypt later” style of attack. In this scenario, adversaries may capture encrypted data today and retain it, planning to decrypt it once they have access to a CRQC. Any sensitive data generated today that will remain sensitive in the future (such as health records) is therefore at risk today.
The Solution: Cryptographic Agility and Post-Quantum Cryptography
So, how can the industry future-proof itself against these threats? The solution is twofold:
- Enabling cryptographic agility: Cryptographic agility is the ability to switch cryptographic systems quickly and efficiently. It’s a forward-looking design principle and capability that helps security interfaces stay flexible and adaptable in the face of all future threats.
- Post-quantum cryptography (PQC): Also called quantum-safe cryptography, these new encryption algorithms are designed to resist attacks from quantum computers. Their standardization, primarily driven by the National Institute of Standards and Technology in the United States, is a global effort that’s been ongoing for the last decade.
PQC aims to be the replacement for today’s vulnerable cryptography. Cryptographic agility is the framework by which systems will be migrated to PQC (and future iterations of cryptographic algorithms). Together, these strategies offer a path forward.
Migrating to PQC and Leveraging Existing Guidance
From existing guidance on cryptographic migrations, the CableLabs Future of Cryptography Working Group — a collaborative initiative bringing together operators, vendors and security experts to prepare for and to navigate changes to evolving cryptography — has identified certain “no-regret” actions, which can benefit network security posture regardless of whether or when the threat of a CRQC is realized. Some of these no-regret actions include:
- Establishing a cryptographic inventory: A comprehensive inventory of what cryptography is deployed is a critical artifact for any organization to compile as a first step towards cryptographic migrations.
- Assessing and estimating cryptographic agility enablement: Cryptographic agility is a deceptively simple concept; effectively enabling it begins with quantifying how cryptographically agile security interfaces are today. Tools exist today to aid in that effort.
- Discussions with vendors: Vendors play a critical role in cryptographic migrations, providing the implementation of security interfaces and concretely enabling cryptographic agility. Therefore, early and ongoing engagement with vendors on their roadmaps for enabling cryptographic agility and migrations to new cryptographic paradigms is key.
- Risk assessments and defining risk tolerance: Migration of cryptography at full organization scale is an optimization problem; undertaking risk assessment activities to identify the devices, services and interfaces that are at highest risk and should be prioritized for migration is crucial.
Taking Action Through Collaboration
Over the next decade, regulatory bodies around the world expect critical infrastructure — including broadband networks — to adopt quantum-safe cryptography. That makes the next five years crucial for operators looking to future-proof their networks and enable cryptographic agility as a key security capability. Reaching that goal will require deep collaboration, not just between network operators, but across the entire ecosystem of equipment manufacturers, software developers and standards organizations.
To ensure a smoother transition, the CableLabs Future of Cryptography Working Group is continuing to drive the foundational work to adapt current crypto migration and agility guidance to cable networks, identifying gaps therein and developing strategies to address those gaps. The working group’s mission is to develop practical, industry-specific guidance for enabling cryptographic agility as a new capability and migrating operator networks to post-quantum cryptography.
The threat may be complex, but the goal for the cable broadband industry is simple: Keep our networks — and the people who rely on them — secure for the future. To learn more or if you’re interested in contributing, the Future of Cryptography Working Group is open to CableLabs members and our vendor community. Join us here.
Security
Hacker Summer Camp 2025 Debrief: AI and the New Threat Landscape

Key Points
- The annual confluence of cybersecurity conferences — known informally as Hacker Summer Camp — drew experts and practitioners from all corners of the cybersecurity ecosystem to Las Vegas in August.
- In this blog post, CableLabs highlights high-level takeaways from the Black Hat USA and DEF CON conferences — with the evolution of AI (and the security gaps arising from it) being a common theme.
- We delve deeper into our insights from the conferences in a new members-only technical brief and will explore the topics further in a CableLabs webinar on Sept. 17.
Last month’s Hacker Summer Camp brought together hackers, researchers, practitioners and leaders in cybersecurity to review the cutting edge of security research, share tools and techniques, and find out what’s at the front of everyone’s mind in the security space.
So, what was at the forefront of the conversation this year in Las Vegas, and what trends in cybersecurity do you need to be aware of?
We outline our takeaways from Black Hat USA and DEF CON in a new CableLabs technical brief, available exclusively for our member operators. We’ll also dive into the conferences further during a members-only webinar on Wednesday, Sept. 17. Members can register here to join us.
For now, some of our high-level insights are summarized here.
What’s Old Is New Again: Hacking Like It’s the 90s
With the rapid adoption of tooling like generative AI and its agentic variants, the implications of overlooking the basics in security are more impactful than ever. Many different presentations at Hacker Summer Camp focused on this theme, in which researchers consistently demonstrated how classic cyberattacks are still thriving, now applied to modern contexts like agentic AI. The takeaway? AI-centric software is still software; thus, the basics apply: applying least privilege, separation of interests, thorough input sanitization and more.
AI: Your New, Non-Deterministic, Insecure Execution Environment
Unsurprisingly, AI remains at the forefront of the discussion. Novel from recent years was the notion that AI is no longer simply a chatbot interface added to your architecture, but a whole new execution environment. Many presentations and demonstrations showcased how large language model (LLM)-powered applications and agentic AI constructions can be abused or confused, with several undesirable outcomes. While there’s a great deal of work to be done to secure emerging AI technologies, many strategies for mitigating attacks were recommended. AI is being adopted in cybersecurity too, from both the adversarial and defender perspectives, which makes it clear that another cybersecurity arms race is underway.
Automation Pitfalls: Deploy Fast, Break Faster — With a Bigger Blast Radius
Automation tooling, such as continuous integration and continuous delivery (CI/CD), took center stage for many discussions, where simple and subtle misconfigurations resulted in significant consequences, from initial access and lateral movement. With one of the killer use cases of agentic AI being coding assistants and source code reviews, today’s relationship between AI and automation tooling is a close one. The aforementioned attack surface of those AI components thus has direct implication to that of the automation tooling.
Initial Access: CI/CD, Developers and Supply Chain Attacks
Finally, the conferences this year demonstrated the increasing burden of developers to act as bastions of security. However, the attack surface faced by the average developer is also increasing. This is due in part to the addition and management of AI assistants with access to code as well as the use of plugins for Integrated Developer Environments (IDEs) like Visual Studio Code that are ubiquitous across the industry. Developers and the tools they interact with are increasingly valuable for adversaries to target, creating opportunities for initial access and even executing supply chain attacks.
Cybersecurity Evolution Continues Moving Forward
Hacker Summer Camp 2025 made it clear that the rapid shifts we’re seeing in technologies like AI have left significant gaps in ensuring that the basics of security remain covered. It also demonstrated that cybersecurity professionals and enthusiasts are doing the work required to address those gaps, as well as adopting new and adapting classic approaches to bolster cybersecurity controls.
To learn more about the content and themes covered during the conferences, download our members-only tech brief and plan to join us Wednesday, Sept. 17, for the Lessons from Hacker Summer Camp 2025 webinar.
If you’re an employee of a CableLabs member operator and don’t yet have an account, register for access to the tech brief and much more member-exclusive content.
Security
Tangled Web: Navigating Security and Privacy Risks of Overlay Networks

Key Points
- By opening their networks to third parties, end users may be inviting risk from botnets, DDoS attacks and other potentially illegal activities.
- Learn how overlay networks function, why deployments of these networks are becoming more common and what the security and privacy risks are for internet service providers and their customers.
Residential proxies and decentralized physical infrastructure networks (DePINs) are technologies that enable end users to participate in semi-anonymous communications similar in function to virtual private networks (VPNs) by essentially sharing their broadband connection with anonymous third-party users. These types of networks are not new, but they have become more popular, easier to set up (sometimes even inadvertently) and are advertised to subscribers to make passive income, remove geo-blocking restrictions, and increase their privacy and security.
In this blog, we’ll look at how these networks function, why subscribers are implementing them on their home networks, and finally the security and privacy risks presented by these types of networks to both subscribers and internet service providers (ISPs).
What Are Overlay Networks?
Generally speaking, overlay networks are logical networks built on top of existing physical networks. Residential proxies and DePINs are examples of overlay networks that consist of software or hardware that runs on the subscriber’s home network or mobile device.
Many of these networks include a crypto token (bitcoin, Ethereum, etc.) that allows the end user to earn a financial stake by sharing their bandwidth in the overlay network. These networks are marketed to subscribers to earn passive income, with catchphrases like, “Get paid for your unused internet” or “Turn your unused internet into cash,” and companies offering these services often have signup bonuses, specials, referral incentive programs and pyramid schemes.
Harms to the Subscriber
End users believe that they will get extra security and privacy by participating in these types of networks. However, they often face a very different reality.
To participate, users must put their trust in the proxy provider, which has strong incentives to monetize their access to end-user data and online activity by selling user information to data brokers or other third parties. For example, privacy violations can occur by leaking sensitive information, such as what sites the subscriber is visiting, to third parties for targeted ads and profiling.
By sharing their broadband connection with these proxy networks, subscribers may unwittingly participate in botnets, distributed denial-of-service (DDoS) attacks and other illegal activities such as copyright violations or, even worse, facilitating the transfer of child sexual abuse material.
The broadband subscriber simply cannot know what undesirable or illegal traffic they are allowing to transit their broadband connection. This can harm the reputation of the subscriber’s IP address, which could result in the subscriber’s access to legitimate services being blocked. It could even result in legal actions against the subscriber as government authorities will track down the often-unwitting subscriber by their IP address.
Additional ways that a broadband subscriber may suffer harm is through the unintentional installation of malware or info-stealing software. For example, a cybercrime campaign by a group named Void Arachne uses a malicious installer for virtual private networks (VPNs) to embed deepfake and artificial intelligence (AI) software to enhance its operations. End users may believe they are installing software that will enhance their privacy and security but are actually installing malware that tracks them and feeds sensitive data to bad actors.
Harms to the Broadband Network
Residential proxies consume bandwidth and produce traffic that is not directed to or originates from the broadband subscriber. This extra bandwidth consumption could adversely affect the subscribers' perceptions of their service and may increase costs for the network operator. There can be implications to peering agreements between operators as well. A residential proxy that facilitates the transfer of certain traffic may lead to lowered reputations of the IP addresses in use and potential blocking by external services.
ISPs face a much broader risk when it comes to IP reputation. The reputation of one IP that has been damaged due to running an overlay network can affect not just one subscriber but multiple subscribers as the IP address is reassigned through Dynamic Host Configuration Protocol (DHCP). If operators use network address translation (NAT), all addresses behind the NAT can be affected. This not only causes disruption in service for the subscribers but can also cause reputational harm to the ISP and its brand.
Some overlay networks require that static inbound port forwarding be set up to fully participate in the network. These ports are then easily scanned and recorded in databases such as Shodan, making participating nodes easy to discover. DePIN hardware will inevitably be deprecated and no longer receive firmware updates and security patches. This will lead to a higher risk of the devices being compromised and exploited for other purposes, such as participating in a botnet.
Improving Capabilities to Counter Threats
In summary, decentralized overlay networks such as residential proxies and DePINs pose real and significant security and privacy concerns for both subscribers and their ISPs. These technologies enable semi-anonymous communications but also increase the risk of reputational harm, disruption in service and potential malicious use.
As these networks become more widespread and are increasingly exploited by malicious actors, it is essential to improve detection capabilities and develop effective mitigation strategies to address these risks.
To effectively mitigate these risks, a multi-stakeholder approach is necessary, involving collaboration between civil society, ISPs, overlay network providers, regulatory bodies and law enforcement agencies. This can include implementing robust network monitoring and security protocols and developing guidelines for educating subscribers on safe usage practices. By taking a proactive and coordinated approach, we can minimize the risks associated with overlay networks and promote a safer and more secure online environment for all users.
If you are a CableLabs member or a vendor and are interested in collaborating with us on solutions for safer, more secure online experiences, explore our working groups and contact us using the button below.
Network as a Service
Empowering the Future of Network Services Through a Federated NaaS Platform

Key Points
- The Federated Developer Portal provides a unified platform for developers to onboard and manage applications across multiple network operators, simplifying Network as a Service access and enhancing scalability, resilience and trust within the ecosystem.
In a world that increasingly depends on digital connections, network as a service (NaaS) has emerged as a game-changing technology. By making network functionalities available as on-demand services across the ecosystem, NaaS empowers developers to build applications that dynamically leverage network resources without needing deep knowledge of the underlying infrastructure. However, as powerful as NaaS is, the process of onboarding developers to access these services remains complex and often inefficient.
To address these challenges, Charter Communications presented a federated approach — the Federated Developer Portal (FDP) — that CableLabs introduced at SCTE TechExpo 2024. The FDP represents a forward-thinking solution that simplifies NaaS access across multiple network operators. This federated model creates a streamlined, secure and scalable environment that allows application developers and operators to collaborate with ease.
The Current Challenges of NaaS at Scale
Although the NaaS APIs that enable developers to create innovative applications are standardized, the processes of onboarding developers and managing applications are not. Because of the current structure, developers must navigate a patchwork of requirements and systems specific to each operator:
- Per-operator onboarding. Developers are often required to individually register and gain approval with each network operator. This process is labor-intensive, repetitive and vulnerable to delay.
- Decentralized integration requirements. Integrating with APIs on a per-operator basis results in diverse, sometimes incompatible processes, creating technical overhead for developers and delaying time to market.
- Single point of failure in centralized systems. When using a centralized model for managing NaaS access, all governance and management operations flow through one system. This approach increases the risk of single points of failure, which can lead to service interruptions or more impactful security vulnerabilities.
Considering these challenges, a federated solution is ideal — one where application developers can register with a consortium of network operators that interoperate at the governance level to manage application developers, applications and their access without compromising trust within the ecosystem. A federated approach offers a resilient, scalable solution that maintains the autonomy of each network operator while giving developers a unified interface for onboarding and management.
What Is the FDP?
The FDP provides a secure, federated platform where network operators and developers interact seamlessly. With FDP, developers can access NaaS capabilities from multiple operators through a single portal, significantly reducing the complexity of onboarding and integration, as well as enabling industry-wide scale. Behind the scenes, trust is maintained through identities based on public key infrastructure (PKI) and the use of digital signatures.
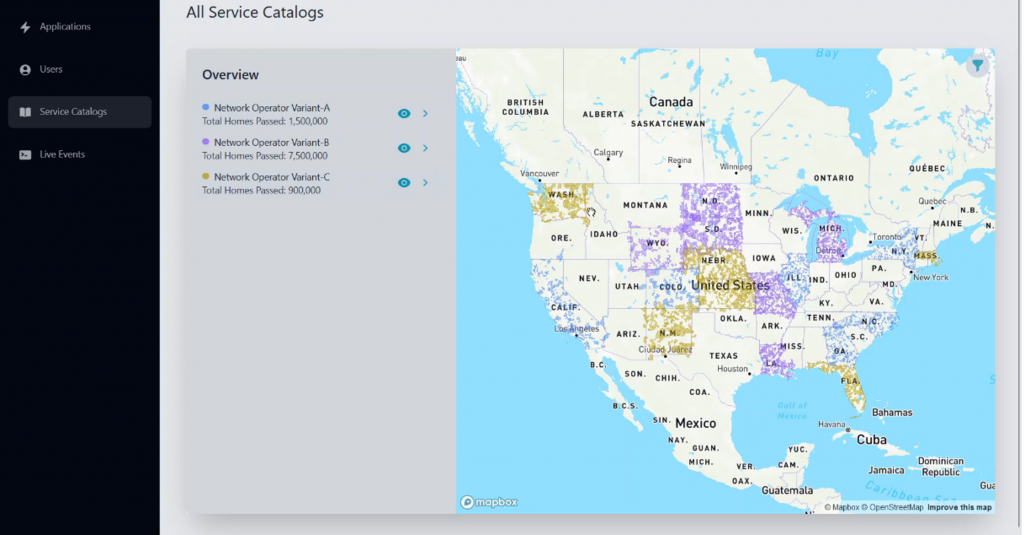
Figure 1: Sample FDP service catalog, from the developer’s perspective
Here are the key features of the FDP:
- Unified interaction point. Network operators and developers have a single, user-friendly interface for application registration, service browsing and management.
- Aggregated service catalogs. Each operator publishes an up-to-date catalog of its available APIs and services, allowing developers to view and select those that suit their applications. This catalog provides essential details, such as API capabilities and supported use cases, giving developers a clear view of network options. Figure 1 provides a sample view of collected service catalogs in our implementation.
- Federated access and approval. Operators retain control over their infrastructure but can securely share service catalogs and API access within the FDP. When developers onboard and submit applications, approval workflows enable each operator to review and approve applications according to its policies, ensuring that only authenticated and authorized applications gain access to network resources.
- Maintained trust. Trust in consortium data is maintained with digital signatures backed by PKI to provide consortium-wide assurance of data integrity and authenticity.
- Modularity. The key components that perform data propagation — the federated agent and the Data Propagation Layer (DPL) — offer an abstraction that enables various propagation technologies, including event streaming, distributed ledgers and more. CableLabs’ key contribution is the definition of governance APIs, which enable flexibility in operator deployment strategy.
An Overview of the Federated Data Portal Architecture
Figure 2 provides a high-level component view of our implementation.
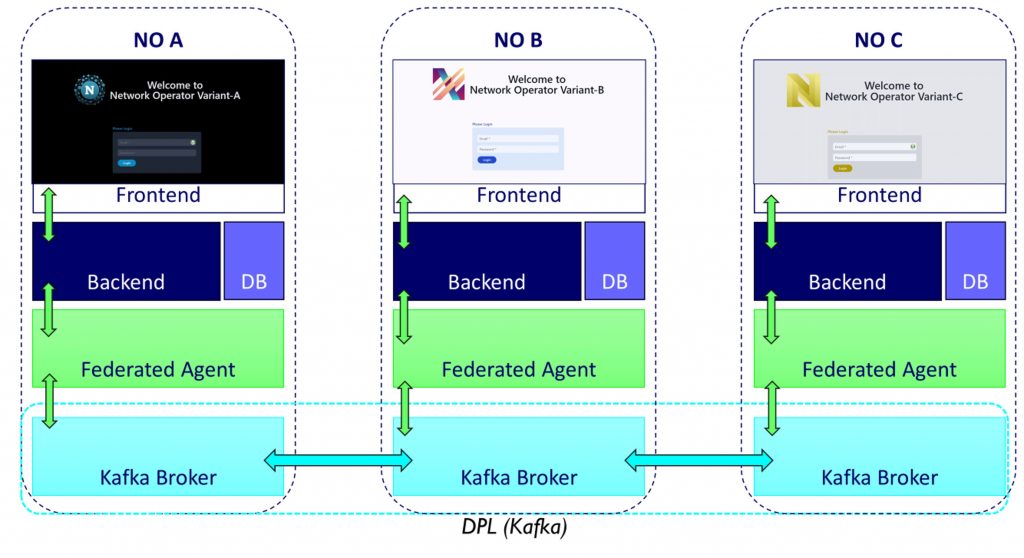
Figure 2: Overview of the FDP architecture
In brief, each network operator deploys a traditional REST API and web interface that application developers can interact with, as well as the components that facilitate data propagation:
- Our DPL is built with Kafka, where governance operations are propagated as events sent to each network operator’s Kafka broker.
- The federated agent is the key element that exposes our governance APIs and enables modularity of the DPL. As the figure shows, the federated agent facilitates propagation by exchanging data with the Kafka layer.
An Example of the Federated Data Flow
Let’s walk through a high-level example of data propagation through the consortium. Imagine that a developer is registering an application with the consortium of network operators through the FDP, as Figure 3 illustrates.
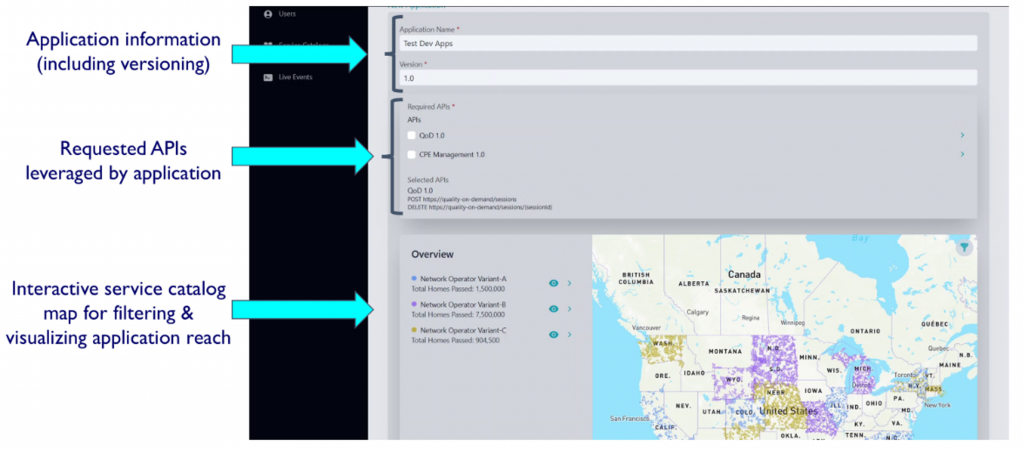
Figure 3: Sample FDP application submission
- Application submission. The developer submits information about his or her application, including which APIs it will leverage. During this step, the developer can see the reach of that application through an informative display of the aggregated service catalogs that the developer has access to. The figure depicts the application submission form of our FDP implementation.
- Consortium data propagation. The submitted information about the new application is propagated to the other network operators via the federated agent and DPL, ensuring that all network operators receive the updated data.
- Approval flow. All network operators have an opportunity to review and approve the new application when it’s received by their deployment.
Key Benefits of the Federated Developer Portal
By adopting the FDP model, both network operators and developers benefit in multiple ways:
- Reduced complexity for developers. Instead of handling onboarding and API integration separately with each operator, developers interact with a single federated system. This one-stop approach allows them to focus on application innovation rather than logistics management.
- Reduced complexity for operators. Operators establish and maintain relationships with a growing number of developers using a single, consistent process, unlocking the full potential of NaaS at scale.
- Increased resiliency for operators. The FDP’s distributed nature eliminates risks tied to single points of failure. Each operator can maintain autonomous operations, ensuring that system outages or vulnerabilities in one part do not affect the entire ecosystem.
- Distributed centralization. The FDP combines the best of both worlds by providing a centralized interface without compromising the decentralized nature of each operator’s control over its infrastructure.
The Future of the FDP
Although the FDP already addresses key challenges, the platform will continue to evolve. Future iterations aim to support advanced provisioning, offer enhanced metadata within service catalogs and improve governance features for seamless operator and developer collaboration.
Possible enhancements on the horizon include:
- Expanded metadata for service catalogs. Adding more detailed descriptions within catalogs will enable developers to choose services more effectively, considering factors such as network capacity, quality tiers and geographic availability.
- Standardized governance APIs. Establishing uniform governance protocols across operators will streamline approval processes, making it easier to manage applications and handle exceptions.
- Enhanced resiliency and state management. The evolution of FDP will incorporate mechanisms to maintain system stability even under complex operational conditions, ensuring continuous service and data consistency.
Join the Federated NaaS Movement
The FDP is more than just a tool; it’s the backbone for the future of network-driven innovation. With a unified platform, secure data exchanges and a distributed model, the FDP is here to empower developers, simplify operations and strengthen the NaaS ecosystem for all.
All this being said, to fully realize the FDP’s potential, we need input and collaboration from network operators, developers and other stakeholders. Your involvement could shape the future of this platform and help drive innovations that will set new standards for network-enabled applications.
If you’re interested in learning more about the FDP or want to see a live demonstration, don’t hesitate to contact our team! Together, we can build a resilient, innovative foundation that will support the next generation of network-based services.
To learn more about NaaS, register for the next CableLabs Live Webinar, “Taking NaaS APIs to Production: Best Practices and Operational Readiness,” exclusively for employees of CableLabs member companies and our NDA vendor community. The webinar on Dec. 11 will include experts from Charter and Vodafone, who will share insights on how they have been able to expose their APIs to offer differentiated services and take those services into production.
Security
Black Hat USA and DEF CON: A Lot to Unpack After “Hacker Summer Camp”

Key Points
- Pervasive and deep understanding is critical for security practitioners in securing their infrastructure.
- Core principles in security are paramount; their ubiquitous application and adherence to both existing and emerging technologies is crucial.
- Advanced technologies and techniques are being adopted by adversaries. To maintain our upper hand, we must carefully embrace the adoption of new technologies as well.
- AI adoption is not slowing down, nor is its application to security use cases or new ways to undermine its security. There continues to be immense potential here.
This year has been a particularly interesting one for cybersecurity. Notable incidents and other areas of focus in cybersecurity set the backdrop for “Hacker Summer Camp 2024” in Las Vegas in August. Topics frequently alluded to during this year’s conferences included:
- Increased focus on critical infrastructure — Critical infrastructure is increasingly complex, distributed and difficult to characterize in terms of security. This year’s conferences accordingly brought an increased attention to securing critical infrastructure.
- Echoes of the CrowdStrike incident — Although the now-infamous CrowdStrike Windows outage in July was a mistake, allusions to lessons that could be learned from the event were often made from the perspective of critical infrastructure security. The outage — and its fallout —prompted discussions about what the impact could be if bad actors were behind a similar incident.
- The XZ Utils (almost) backdoor — The discovery of the XZ Utils backdoor in early 2024 — the focus of a dedicated talk at DEF CON — serves as a reminder of the growing sophistication of adversaries.
I’ve published a CableLabs Technical Brief to share my key takeaways from this mega cybersecurity event that combined the Black Hat USA 2024 and DEF CON 32 conferences. In addition to covering the highlights of talks and demos I attended, this Tech Brief delves deeply into the discussions I found to be most insightful and the commonalities I observed across several areas of the conferences.
There’s no denying that “Hacker Summer Camp” offers more than any one person could hope to see or do on the conference floor in a single day. Each conference was packed with a wealth of new research and perspectives, demonstrations and much more. Still, the key highlights in my Tech Brief provide a solid and in-depth overview of some of the most talked-about topics and issues existing today in the field of cybersecurity.
I’ve included more quick takeaways below, and CableLabs members looking for a more comprehensive debrief can download the Tech Brief.
Common Ties at Black Hat USA and DEF CON
I found that topics from the presentations, demonstrations and conversations at Black Hat and DEF CON fell into three overarching themes. I expand on the implications of these in the tech brief.
Deep (human) learning: A need for more pervasive understanding
Doing rigorous background research is key to gaining an upper hand in innovating and building strong security postures. Especially in light of rapid adoption of advanced technologies, security experts need to deepen their knowledge to better secure their infrastructure. Collaboration is also a crucial element of building deeper bases of knowledge on technical topics.
Back to basics: Returning to and applying core principles
The core principles of cybersecurity are foundational to maintaining a strong security posture when implementing, deploying or maintaining any technology. As security researchers and practitioners, part of our role is to see through the use cases toward the misuse cases as a first step to ensuring the fundamentals are there and to educate and empower others to do the same.
Inevitabilities and cybersecurity: What we must embrace and why
My Tech Brief elaborates on examples in which adversaries will adopt and take advantage of new technologies, regardless of our own adoption. There are always caveats and important details that must be accounted for to ensure the secure use of new technologies as they are adopted. However, the Tech Brief discusses how the potential benefits to bolster security that come with the thoughtful adoption of new technologies often significantly outweigh the risks that they introduce.
AI’s Rapid Adoption, Potential and Pitfalls
AI once again took center stage (including at Black Hat’s inaugural AI Summit). Particularly in focus were agentic AI, assistants and RAG-enhanced LLMs. Like last year, these tools were looked at through the (mostly mutually exclusive) lenses of “AI for security applications” and considerations of “the security of AI,” both of which present immense opportunities for research and innovation.
Download the Tech Brief to read my takeaways from notable talks about this from the conferences.
Building More Secure Networks Together
It’s a thrilling time in cybersecurity! With all of the innovations, perspectives and calls to action seen at Black Hat USA and DEF CON this year, it’s clear that there’s a lot of work to be done.
To read more from my debrief, download our members-only Tech Brief. Our member and vendor community can get involved in this work by participating in CableLabs’ working groups.
Did you know?
In addition to in-depth tech briefs covering events like this, CableLabs publishes short event recap reports — written by our technologists, exclusively for our members. Catch up on recent recaps (member login required).
Security
CableLabs Co-Chairs New M3AAWG AI Committee
Key Points
- M3AAWG has formed the AI Committee to proactively address challenges posed by the increased use of artificial intelligence in online abuse.
- Addressing AI-powered abuse, the committee will study abusers' tactics and develops best practices to mitigate the impact of spam, phishing, fraud and online harassment.
- Actively tracking and advocating for responsible AI development policies, efforts are directed towards enhancing AI system security and ensuring lifecycle protection against cyber threats.
The sudden rise of highly capable artificial intelligence (AI) has brought immense opportunities for beneficial innovation and advancement. However, alongside its benefits, AI also presents unique challenges concerning online abuse and threats to security and privacy. Recognizing the urgency of addressing these issues, the Messaging, Malware, and Mobile Anti-Abuse Working Group (M3AAWG) has taken a proactive stance by forming a dedicated AI Committee. The M3AAWG AI Committee, co-chaired by CableLabs, underscores M3AAWG’s commitment to fostering a safer and more secure online environment for users worldwide.
Tackling Abuse Facilitated by AI Systems
One of the primary objectives of the M3AAWG AI Committee is to address the growing concern surrounding malicious actions facilitated by AI systems. To bolster spam and phishing attacks, fraud, and online harassment, nefarious actors are increasingly leveraging AI-powered tools to amplify and accelerate their harmful activities. By studying the tactics employed by abusers and evaluating countermeasures, the committee aims to develop best common practices to help mitigate the impact of AI-facilitated abuse on individuals and organizations alike.
Public Policy and AI Abuse
The landscape of AI policy is in varying stages of development, with governmental and intergovernmental bodies around the globe proposing and enacting their own models of regulation and oversight. These efforts include the recent Executive Order in the United States aiming for "Safe, Secure, and Trustworthy Development and Use of Artificial Intelligence," and the European Union’s proposed AI Act establishing stricter regulations for high-risk applications. The M3AAWG AI Committee is establishing an initiative to track policy developments and advocate for public policy promoting responsible and secure AI development.
Best Common Practices for Securing the AI Lifecycle and AI Systems
As AI technologies become more pervasive across various sectors, they also become prime targets for cyberattacks and exploitation. Vulnerabilities in AI algorithms and frameworks can be exploited to manipulate outcomes, compromise data integrity, and undermine trust in AI-driven solutions. In addition to combating malicious use, the M3AAWG AI Committee is focused on enhancing the security of AI systems and the AI lifecycle from training to deployment of AI models through the development of best common practices.
Harnessing AI to Counter Abuse
Although AI has been weaponized for nefarious purposes, it also holds immense potential as a tool for combating abuse and safeguarding online ecosystems. The M3AAWG AI Committee recognizes this dichotomy and is exploring innovative ways to harness AI for good. From proactive content moderation and anomaly detection to sentiment analysis and behavioral profiling, AI technologies offer many possibilities for enhancing online safety and security. By developing AI-driven solutions for detecting and mitigating abuse in real-time, the committee aims to empower service providers, platforms, and other stakeholders in their efforts to combat online threats effectively.
Why M3AAWG: Collaboration and Engagement
M3AAWG recently celebrated 20 years of combating online abuse and making the internet a safer place. The last 20 years of combating spam, malware, DDoS and many other forms of abuse has only been possible through collaboration and engagement with industry leaders, academic institutions, government agencies, and advocacy groups. The M3AAWG AI Committee will leverage and build upon these relationships within the unique trusted forum of M3AAWG to address the complex challenges posed by AI-driven abuse and innovate towards AI-enabled solutions. Through open dialogue, knowledge sharing, and collaborative initiatives, the M3AAWG AI Committee aims to foster a community-driven approach to combating online abuse and promoting responsible AI usage.
Looking Ahead: The Next 20 Years
As AI continues to evolve at a rapid pace, the importance of proactive measures to address its implications for online abuse and security cannot be overstated. With the establishment of the AI Committee at its 60th meeting in San Francisco this February, M3AAWG has taken a significant step towards addressing these pressing issues head-on. By leveraging collective expertise and resources, the committee is poised to drive meaningful progress in safeguarding the digital landscape against emerging threats.
Stay tuned for updates and insights from M3AAWG as we continue our journey towards a safer digital future, and please consider joining M3AAWG and the AI Committee to do your part.

Security
Maintaining Confidentiality in the 10G Network

The 10G platform will offer almost limitless opportunities for innovation and new experiences in the home, bolstering the capabilities of the Internet of Things (IoT) landscape. While the volume of data that passes over cable technologies continues to grow, the classification of private and confidential boundaries continues to change.
Moreover, security is an abstract topic, particularly in the sense of the assurance it provides. We expect security to be present, but in a way that we don’t need to think about; we expect the assurance of security to be seamless. Behind the scenes, security is a constant source of innovation to make that seamless protection possible in the face of an ever-changing set of vulnerabilities, threats and exploits. The frequent application of the phrase “arms race” to describe that innovation is appropriate. Addressing confidentiality is a key pillar in the 10G security platform; it ensures that user data continues to be protected as new possibilities and services become available.
Brief Review: What Is Confidentiality?
Last fall, CableLabs produced a set of blog posts covering the security pillars of confidentiality, integrity and availability. Confidentiality ensures that access to resources such as hardware components, sensor data or private information is only granted to authorized actors, whether they’re users or processes. Authorization is part of the mechanism that enables confidentiality as the barrier between the actor and resource.
What are the primary ways that we can keep information confidential? We’re going to focus on two techniques applied to information:
- Encryption-Using algorithms to render information unreadable without the proper materials (keys) to decrypt it.
- Separation and Isolation-Putting barriers in place that must be traversed before gaining access to information.
In addition, there are some threats against confidentiality, including vulnerabilities in encryption algorithms, exploits that can circumvent authorization mechanisms, and, of course, there’s the possibility of quantum computing right around the corner. To stay ahead of the curve, we must continue to innovate to meet these threats.
Where Confidentiality Counts: The Network
Confidentiality is key when it comes to the amount of data that passes between machines. Even over the past 5 years, the data that we consider to be critical in terms of confidentiality has evolved beyond simply what we’re browsing or streaming. It’s also about what our devices are doing.
In the age of the IoT, where every device is connected and often eager to capture the aspects of our environment or actions it invokes, confidentiality also applies to the data that is shared between devices and their cloud services. A great amount can be garnered from the passive observations and actions of smart devices as they’re used over time, including behaviors typical of users interacting with them (e.g., when the smart coffee pot is typically started in the morning). Protecting such data at home is particularly paramount during these unprecedented times of increased “work-from-home” routines.
Continuing to Ensure Confidentiality on the Network
Since its inception in 1997, the DOCSIS ® specification (and later the extended DOCSIS ® security specification) have implemented encryption to ensure that user data is protected from eavesdropping on the cable network. Over the years, changes to encryption algorithms and key sizes have been enacted in DOCSIS in line with the recommendations and best practices of industry and standards organizations.
As the threats against confidentiality continue to be revealed in the world of 10G, CableLabs will continue to adapt to the cryptographic standards and recommendations of such groups through updates to specifications and best practices. Future innovations in encryption technologies will continue to accommodate the incredible power of the 10G network while ensuring the confidentiality of the data that is carried over it.
Maintaining Confidentiality in the Age of the Smart Home
A major evolution in the architecture of the Internet that has come about in only the past decade has been the advent of the IoT. As noted before, confidential data and its privacy implications are now more prevalent than ever, even within only a single smart home. In addition, it may be possible for one compromised smart device to act as a starting point for further intrusions of other devices or points in the home; how can we utilize separation to protect against such a scenario?
Enter CableLabs Micronets, a system that can dynamically organize devices into different groups and provide network separation among them. With this system enabled on your home (or work) networks, one compromised device doesn’t directly provide an attacker with the possibility to target other devices and/or confidential data they may have stored or transmitted over the network.
As for confidentiality when devices talk to each other, CableLabs continues to engage with standards organizations such as OCF to draft standards that ensure the secure operation (and interoperation) of IoT devices, as well as device interactions with cloud services.
Conclusions
The opportunities that the 10G platform will provide are immense in both promise and scope, allowing previously infeasible technologies to be brought to the forefront to provide new classes of products and services.
In light of these great innovations, we must remain cognizant when it comes to the confidentiality of our resources and the protection of user data. As the “arms race” continues, we will continue innovating and staying one step ahead. That’s the speed of security.