Security
A Unified Approach to AI Security in the Broadband Industry
Key Points
- AI has the potential to transform networks to be smarter, more adaptable and more reliable; however, this rapid evolution introduces new and complex security challenges.
- CableLabs is launching the AI Security Working Group to bring well-understood security principles into AI R&D, promoting best practices and practical security guidance for AI development to secure the cable broadband industry’s critical infrastructure.
AI is turning the vision of pervasively intelligent networks into reality. It’s becoming the driving force behind networks that are smarter, more adaptable, more reliable and more secure than ever. No longer limited to generating text, AI is evolving into an active operational agent within cable networks. It’s an evolution that unlocks unprecedented opportunities for innovation and new subscriber experiences.
However, this transformation also introduces new and complex security challenges.
Managing the Challenges of AI
Many of AI’s challenges stem from the relentless pace of innovation. New protocols, tools and methods are adopted soon after they emerge, leaving security as an afterthought. For instance, some AI agents are capable of autonomously interacting with data, using tools and calling APIs. All of this adds new layers of complexity, dependencies and attack surfaces. These risks should be carefully managed and addressed as early as possible in the design and development stages.
A key element in any risk management framework is grounding this innovation in a secure foundation that spans the entire AI stack, from the large language models (LLMs) at the core, to the AI agents and their prompts, to the tools and APIs they use, and finally to the AI protocols that connect and coordinate them.
CableLabs is investigating cable-specific elements where we can bring well-understood security principles into AI R&D, laying the foundation of protecting cable’s critical infrastructure from tampering and subversion. Just like any other software, the AI stack would benefit from provenance guarantees, integrity, identity assertions and transitive credentialing.
The AI Security Working Group
Because AI architectures interact directly with critical systems and sensitive data, securing the entire ecosystem — from clients and servers to the protocols that link them — isn’t just a technical best practice; it’s a strategic imperative for the industry. A unified focus on AI security will enable trusted communications and accelerate innovation across both business and technical domains.
To foster collaborative input and discussion, CableLabs is launching the AI Security Working Group (AISWG), a CableLabs member initiative focused on developing and promoting best common practices and practical security guidance for AI deployment relevant to the cable broadband industry. By bringing our members together in this forum, we can help our industry harness the transformative power of AI confidently, responsibly and securely.
CableLabs is also actively engaged in two other non-cable groups working on securing AI:
- The Messaging Malware Mobile Anti-Abuse Working Group (M3AAWG) is working on preventing abuse of and abuse from AI systems.
- The Open Worldwide Application Security Project (OWASP) is working on a broad range of threats to AI.
How You Can Help
There are a few ways CableLabs members can be part of this essential initiative:
- Maximize your membership: Register for a CableLabs account to explore exclusive, member-only resources and content.
- Join the working group: Request to join the AI Security Working Group, and help us define the future of AI security. (A CableLabs account is required to log in.)
- Connect with us: Introduce us to the people in your organization who are focused on AI security, governance and agent protocol implementation.
Security
Tangled Web: Navigating Security and Privacy Risks of Overlay Networks

Key Points
- By opening their networks to third parties, end users may be inviting risk from botnets, DDoS attacks and other potentially illegal activities.
- Learn how overlay networks function, why deployments of these networks are becoming more common and what the security and privacy risks are for internet service providers and their customers.
Residential proxies and decentralized physical infrastructure networks (DePINs) are technologies that enable end users to participate in semi-anonymous communications similar in function to virtual private networks (VPNs) by essentially sharing their broadband connection with anonymous third-party users. These types of networks are not new, but they have become more popular, easier to set up (sometimes even inadvertently) and are advertised to subscribers to make passive income, remove geo-blocking restrictions, and increase their privacy and security.
In this blog, we’ll look at how these networks function, why subscribers are implementing them on their home networks, and finally the security and privacy risks presented by these types of networks to both subscribers and internet service providers (ISPs).
What Are Overlay Networks?
Generally speaking, overlay networks are logical networks built on top of existing physical networks. Residential proxies and DePINs are examples of overlay networks that consist of software or hardware that runs on the subscriber’s home network or mobile device.
Many of these networks include a crypto token (bitcoin, Ethereum, etc.) that allows the end user to earn a financial stake by sharing their bandwidth in the overlay network. These networks are marketed to subscribers to earn passive income, with catchphrases like, “Get paid for your unused internet” or “Turn your unused internet into cash,” and companies offering these services often have signup bonuses, specials, referral incentive programs and pyramid schemes.
Harms to the Subscriber
End users believe that they will get extra security and privacy by participating in these types of networks. However, they often face a very different reality.
To participate, users must put their trust in the proxy provider, which has strong incentives to monetize their access to end-user data and online activity by selling user information to data brokers or other third parties. For example, privacy violations can occur by leaking sensitive information, such as what sites the subscriber is visiting, to third parties for targeted ads and profiling.
By sharing their broadband connection with these proxy networks, subscribers may unwittingly participate in botnets, distributed denial-of-service (DDoS) attacks and other illegal activities such as copyright violations or, even worse, facilitating the transfer of child sexual abuse material.
The broadband subscriber simply cannot know what undesirable or illegal traffic they are allowing to transit their broadband connection. This can harm the reputation of the subscriber’s IP address, which could result in the subscriber’s access to legitimate services being blocked. It could even result in legal actions against the subscriber as government authorities will track down the often-unwitting subscriber by their IP address.
Additional ways that a broadband subscriber may suffer harm is through the unintentional installation of malware or info-stealing software. For example, a cybercrime campaign by a group named Void Arachne uses a malicious installer for virtual private networks (VPNs) to embed deepfake and artificial intelligence (AI) software to enhance its operations. End users may believe they are installing software that will enhance their privacy and security but are actually installing malware that tracks them and feeds sensitive data to bad actors.
Harms to the Broadband Network
Residential proxies consume bandwidth and produce traffic that is not directed to or originates from the broadband subscriber. This extra bandwidth consumption could adversely affect the subscribers' perceptions of their service and may increase costs for the network operator. There can be implications to peering agreements between operators as well. A residential proxy that facilitates the transfer of certain traffic may lead to lowered reputations of the IP addresses in use and potential blocking by external services.
ISPs face a much broader risk when it comes to IP reputation. The reputation of one IP that has been damaged due to running an overlay network can affect not just one subscriber but multiple subscribers as the IP address is reassigned through Dynamic Host Configuration Protocol (DHCP). If operators use network address translation (NAT), all addresses behind the NAT can be affected. This not only causes disruption in service for the subscribers but can also cause reputational harm to the ISP and its brand.
Some overlay networks require that static inbound port forwarding be set up to fully participate in the network. These ports are then easily scanned and recorded in databases such as Shodan, making participating nodes easy to discover. DePIN hardware will inevitably be deprecated and no longer receive firmware updates and security patches. This will lead to a higher risk of the devices being compromised and exploited for other purposes, such as participating in a botnet.
Improving Capabilities to Counter Threats
In summary, decentralized overlay networks such as residential proxies and DePINs pose real and significant security and privacy concerns for both subscribers and their ISPs. These technologies enable semi-anonymous communications but also increase the risk of reputational harm, disruption in service and potential malicious use.
As these networks become more widespread and are increasingly exploited by malicious actors, it is essential to improve detection capabilities and develop effective mitigation strategies to address these risks.
To effectively mitigate these risks, a multi-stakeholder approach is necessary, involving collaboration between civil society, ISPs, overlay network providers, regulatory bodies and law enforcement agencies. This can include implementing robust network monitoring and security protocols and developing guidelines for educating subscribers on safe usage practices. By taking a proactive and coordinated approach, we can minimize the risks associated with overlay networks and promote a safer and more secure online environment for all users.
If you are a CableLabs member or a vendor and are interested in collaborating with us on solutions for safer, more secure online experiences, explore our working groups and contact us using the button below.
Security
CableLabs Co-Chairs New M3AAWG AI Committee
Key Points
- M3AAWG has formed the AI Committee to proactively address challenges posed by the increased use of artificial intelligence in online abuse.
- Addressing AI-powered abuse, the committee will study abusers' tactics and develops best practices to mitigate the impact of spam, phishing, fraud and online harassment.
- Actively tracking and advocating for responsible AI development policies, efforts are directed towards enhancing AI system security and ensuring lifecycle protection against cyber threats.
The sudden rise of highly capable artificial intelligence (AI) has brought immense opportunities for beneficial innovation and advancement. However, alongside its benefits, AI also presents unique challenges concerning online abuse and threats to security and privacy. Recognizing the urgency of addressing these issues, the Messaging, Malware, and Mobile Anti-Abuse Working Group (M3AAWG) has taken a proactive stance by forming a dedicated AI Committee. The M3AAWG AI Committee, co-chaired by CableLabs, underscores M3AAWG’s commitment to fostering a safer and more secure online environment for users worldwide.
Tackling Abuse Facilitated by AI Systems
One of the primary objectives of the M3AAWG AI Committee is to address the growing concern surrounding malicious actions facilitated by AI systems. To bolster spam and phishing attacks, fraud, and online harassment, nefarious actors are increasingly leveraging AI-powered tools to amplify and accelerate their harmful activities. By studying the tactics employed by abusers and evaluating countermeasures, the committee aims to develop best common practices to help mitigate the impact of AI-facilitated abuse on individuals and organizations alike.
Public Policy and AI Abuse
The landscape of AI policy is in varying stages of development, with governmental and intergovernmental bodies around the globe proposing and enacting their own models of regulation and oversight. These efforts include the recent Executive Order in the United States aiming for "Safe, Secure, and Trustworthy Development and Use of Artificial Intelligence," and the European Union’s proposed AI Act establishing stricter regulations for high-risk applications. The M3AAWG AI Committee is establishing an initiative to track policy developments and advocate for public policy promoting responsible and secure AI development.
Best Common Practices for Securing the AI Lifecycle and AI Systems
As AI technologies become more pervasive across various sectors, they also become prime targets for cyberattacks and exploitation. Vulnerabilities in AI algorithms and frameworks can be exploited to manipulate outcomes, compromise data integrity, and undermine trust in AI-driven solutions. In addition to combating malicious use, the M3AAWG AI Committee is focused on enhancing the security of AI systems and the AI lifecycle from training to deployment of AI models through the development of best common practices.
Harnessing AI to Counter Abuse
Although AI has been weaponized for nefarious purposes, it also holds immense potential as a tool for combating abuse and safeguarding online ecosystems. The M3AAWG AI Committee recognizes this dichotomy and is exploring innovative ways to harness AI for good. From proactive content moderation and anomaly detection to sentiment analysis and behavioral profiling, AI technologies offer many possibilities for enhancing online safety and security. By developing AI-driven solutions for detecting and mitigating abuse in real-time, the committee aims to empower service providers, platforms, and other stakeholders in their efforts to combat online threats effectively.
Why M3AAWG: Collaboration and Engagement
M3AAWG recently celebrated 20 years of combating online abuse and making the internet a safer place. The last 20 years of combating spam, malware, DDoS and many other forms of abuse has only been possible through collaboration and engagement with industry leaders, academic institutions, government agencies, and advocacy groups. The M3AAWG AI Committee will leverage and build upon these relationships within the unique trusted forum of M3AAWG to address the complex challenges posed by AI-driven abuse and innovate towards AI-enabled solutions. Through open dialogue, knowledge sharing, and collaborative initiatives, the M3AAWG AI Committee aims to foster a community-driven approach to combating online abuse and promoting responsible AI usage.
Looking Ahead: The Next 20 Years
As AI continues to evolve at a rapid pace, the importance of proactive measures to address its implications for online abuse and security cannot be overstated. With the establishment of the AI Committee at its 60th meeting in San Francisco this February, M3AAWG has taken a significant step towards addressing these pressing issues head-on. By leveraging collective expertise and resources, the committee is poised to drive meaningful progress in safeguarding the digital landscape against emerging threats.
Stay tuned for updates and insights from M3AAWG as we continue our journey towards a safer digital future, and please consider joining M3AAWG and the AI Committee to do your part.

Security
Cybersecurity Awareness Month and Beyond: How We’re Safeguarding Network Integrity
In the digital age, cybersecurity is the first line of defense against an ever-expanding and continually evolving array of threats. The increasing sophistication of cyber threats and a deepening dependence on interconnectivity have elevated cybersecurity technologies from a peripheral consideration to a critical priority.
October is Cybersecurity Awareness Month, but safeguarding digital integrity is a year-round commitment for CableLabs. In our Security Lab, we work to identify and mitigate threats to the access network. We proactively develop innovative technologies that make it easier for internet users to protect their digital lives.
Let’s take a look at some of the CableLabs technologies that are enhancing network security and reshaping the way we protect ourselves online.
DOCSIS 4.0 Security
The new DOCSIS® 4.0 protocol is another promising chapter in the successful life of hybrid fiber coax (HFC) networks, and it brings with it notable security enhancements to the broadband community.
It’s important to note that DOCSIS 4.0 cable modems (CMs) are compatible with existing DOCSIS 3.1 networks. This allows the CMs to take advantage of higher speed tiers even without needing to upgrade the network at the same time. To fully leverage the new upstream bandwidth efficiency and security features of the protocol, both modems and cable modem termination systems (CMTSs) need to support DOCSIS 4.0 technology.
Another key security-enhancing element of the technology is that DOCSIS 4.0 networks come with upgradable security. The technology continues to support the Baseline Privacy protocol (BPI+ V1) used in DOCSIS 3.1 specifications. It also integrates the new version that can be enabled as needed (BPI+ V2).
The new version introduces mutual authentication between devices and the network, eliminates the dependency on the Rivest Shamir Adleman (RSA) algorithm and implements modern key exchange mechanisms. This change enhances device authentications with Perfect Forward Secrecy and cryptographic agility and aligns DOCSIS key exchange mechanisms with the latest Transport Layer Security (TLS) protocol, v1.3.
Further upgrades include enhanced revocation-checking capabilities with support for both Online Certificate Status Protocol (OCSP) and Certificate Revocation List (CRL) in DOCSIS 4.0 certificates. DOCSIS 4.0 also introduces standardized interfaces for managing edge device access (SSH) aimed at limiting the exposure of corporate secrets (e.g., technicians’ passwords) and incorporates a Trust on First Use (TOFU) approach for downgrade protection across BPI+ versions.
Ultimately, the new DOCSIS 4.0 security is designed to provide several options for network risk management. These features include new speeds and capabilities that can be utilized alongside today’s security properties and procedures (e.g., BPI+V1 with DOCSIS 3.1 or DOCSIS 4.0 CMTSs) and advanced protections when needed.
Matter Device Onboarding
Passwords are meant to be secret, so why are users sharing them with all of their Internet of Things (IoT) devices? At CableLabs, we’re working to make it easy for end-users to add devices to their home networks without needing to share a password with every device.
Because so many devices are communicating with one another, standardization is critical — especially when it comes to security. That’s where Matter comes in. The open-source connectivity standard is designed to enable seamless and secure connectivity among the devices in users’ smart home platforms.
Our vision is for each device to have its own credential to get on the Wi-Fi network. The access point (AP) would use this unique credential to grant the device access to the network, and the device then would verify the AP’s credential. This has three incredibly significant advantages for subscribers:
1. It vastly increases the security of the home network. This is because a compromised device cannot divulge a global network password and lead to a compromise of the entire network.
2. It’s possible to leverage the device attestation certificate that comes with every Matter device to inform the network that it’s a verified and certified device.
3. There's no need to reset every single device on the network if the Wi-Fi password is changed.
Join us for a demonstration of Matter at SCTE® Cable-Tec Expo®, which is October 17–19 in Denver, Colorado. Come see us in CableLabs’ booth 2201 to see the future of networked IoT devices and how scanning a QR code can get a device on a network with its own unique credential.
CableLabs Custom Connectivity for MDUs
One of the fastest-growing market segments for broadband providers worldwide is the multi-dwelling unit (MDU) segment. The opportunities here include fast-growing apartment communities, as well as segments such as emergency/temporary housing, low-cost housing, the hospitality and short-term rental markets, and even emergency services.
A common theme across these is the need for an alternate deployment model that allows on-demand service activation and life-cycle management, as well as custom connectivity to various devices. The traditional deployment model of installing customer premises equipment (CPE) on a per-subscriber and/or per-unit basis has hindered operators in delivering services to these segments in a cost-effective manner.
The CableLabs Custom Connectivity architecture is designed to address these constraints by providing dynamic, on-demand subscription activation and device-level management to consumers across the operator’s footprint — without the need to deploy a CPE. The architecture leverages the security controls and mechanisms designed within the CableLabs Micronets technology to provide dynamic, micro-segmentation-based subscription delivery where a subscriber’s devices can connect to their “home subscription” from anywhere on the network and across different access technologies (Wi-Fi, cellular, etc.).
Additionally, it provides consistent operational interfaces for device authentication and service provisioning, as well as billing and subscription management interfaces to enable on-the-fly subscription activation and management.
Safer Networks, Empowered Users
The importance of proactive cybersecurity measures can’t be overstated, and these cutting-edge technologies are proof of CableLabs’ ongoing commitment to enhancing network security. These innovations not only make our networks safer, but they also empower users to take charge of their own online security.
By staying at the forefront of cybersecurity advancements, CableLabs continues to ensure we can all navigate the digital world with greater confidence and peace of mind.

Security
Securing IoT Networks: NCCoE and CableLabs Collaborate to Develop Trusted Onboarding Solution

Billions of Internet of Things (IoT) devices have been added to the internet over the past several years. During that time, millions of insecure IoT devices have contributed to massive Distributed Denial of Services (DDoS) attacks, exposing end users’ private data. To address the problem of insecure IoT devices, CableLabs participates in and contributes to several industry standards development organizations with the goal of building security into the very foundation of new devices and IoT protocols. This work culminates in the release of Matter 1.0, a secure interoperable IoT specification that major industry players are rapidly adopting.
Secure IoT Onboarding
The next critical challenge in enhancing IoT security is to extend interoperability between devices and the networks that connect them. Smart-home networks must be able to facilitate the addition of new devices, validate devices that are connected, help ensure that those devices are fully patched and updated, and safely isolate them if they’re vulnerable.
The next generation of smart-home networking begins with connecting the devices securely the first time. It’s no longer sufficient or secure to ask that consumers share their Wi-Fi password with every device on their smart home network. The network must be smart enough to give each device its own credentials to connect to the network. Crucially, the process for adding (also called onboarding) a device to the smart home network must be simple, seamless and secure.
Industry and Government Collaboration
To address this challenge, CableLabs has joined the National Cybersecurity Center of Excellence (NCCoE) Trusted Device Network-Layer and Lifecycle Management. CableLabs and 10 other companies have been collaborating to develop a reliable network-layer onboarding solution for all IoT devices. This solution leverages established non-proprietary standards and protocols, offering secure onboarding while providing device identification, authentication and authorization. This project covers the following objectives:
- Provide the device with unique network credentials that can be updated securely and automatically, allowing the network to authenticate the device and eliminating the need for a shared password across all IoT devices.
- Employ a secure network-layer protocol to facilitate the secure and automatic provisioning of devices with both network and application-layer credentials for connecting with other devices and the cloud.
- Demonstrate successful interoperability between devices built and configured by participating industry collaborators.
Streamlining the User Experience
CableLabs’ contributions to the Trusted Device Network-Layer and Lifecycle Management project harness the simplicity of Wi-Fi Easy Connect from the Wi-Fi Alliance, the secure interoperability of IoTivity from Open Connectivity Foundation and the powerful technology behind CableLabs’ Micronets to create a secure and streamlined process that allows users to onboard, provision and secure devices on their smart-home networks in a single intuitive step.
CableLabs’ involvement in the Trusted Device Network-Layer and Lifecycle Management project underscores its commitment to advancing IoT security and developing best practices for secure and effortless device onboarding. By collaborating with other industry leaders, CableLabs aims to promote the adoption of secure IoT technologies and ensure that consumers have access to reliable and user-friendly solutions for managing their connected devices.
A draft of this work can be found at NIST Special Publication (SP) 1800.

Security
With Great Bandwidth Comes Great Responsibility
Cable's next generation, 10G networks, holds the promise to deliver symmetrical multi-gigabit speeds that are 100 times faster than what some consumers are currently experiencing today. This great leap forward will enable services and experiences that will drive internet innovation for years to come. It is our mutual responsibility to assure that devices we connect to these blazing 10 gigabit internet connections, are updated and patched, free from default passwords and use proper authentication and authorization.
The lack of following basic cyber-security principals surfaced in the late Fall of 2016, when many popular sites such as Twitter, Amazon, Reddit and Netflix, were unreachable for several periods, lasting hours. The cause was a massive distributed denial of service (DDoS) attack coming from hundreds of thousands of compromised internet of things (IoT) devices. Traffic from these devices overwhelmed the DNS service provider dyn.com and effectively blocked customers and users from reaching these popular Internet locations for hours at a time.
As we approach a world where households are connected at gigabit and greater speeds, building secure devices and getting them in the hands of consumers is essential. Over the last several years CableLabs has been engaged with standard organizations such as, the Consumer Technology Association (CTA) and the Open Connectivity Foundation (OCF), to draft specifications and guide security baselines for IoT devices. This work has culminated in the release of OCF's international ISO\IEC specification for IoT interoperability.
The OCF specification brings together over 450 member companies and work that spans half a decade to apply cyber-security best practices to the IoT. This specification, combined with an open source reference implementation, seven approved global testing and certification labs and an active community of practitioners and member companies (from device vendors, network device venders and network operators), is uniquely positioned to be the secure standard that unites the industry.
With the OCF specification a consumer can buy a certified device from Vendor A and be confident in the knowledge that not only will it work with their certified appliance from Vender B, but it will do so in a way that is encrypted and authenticated. OCF can work with many cloud services but does not inherently need the cloud, promising consumers a good balance between the convenience of the cloud and the privacy and availability of their local networks.
The OCF specification's security-first approach brings it into close alignment with several of the security guidelines from government and industry, including:
- National Institute for Standards and Technology (NIST) NISTIR 8259 draft of recommendations IoT device manufacturers.
— OCF meets 6/6 requirements - The Consumer Technology Association (CTA) C2 Consensus on IoT Device Security Baseline Capabilities.
— OCF meets 10/10 requirements - UK's Code of Practice for Consumer IoT Security.
— OCF meets 11/13 requirements (other two requirements are aimed at service providers not device requirements) - European Union Agency for CyberSecurity (ENISA) Baseline Security Recommendations for IoT.
— OCF meets 40/57 requirements (most unmet requirements are not applicable to a device centric model)
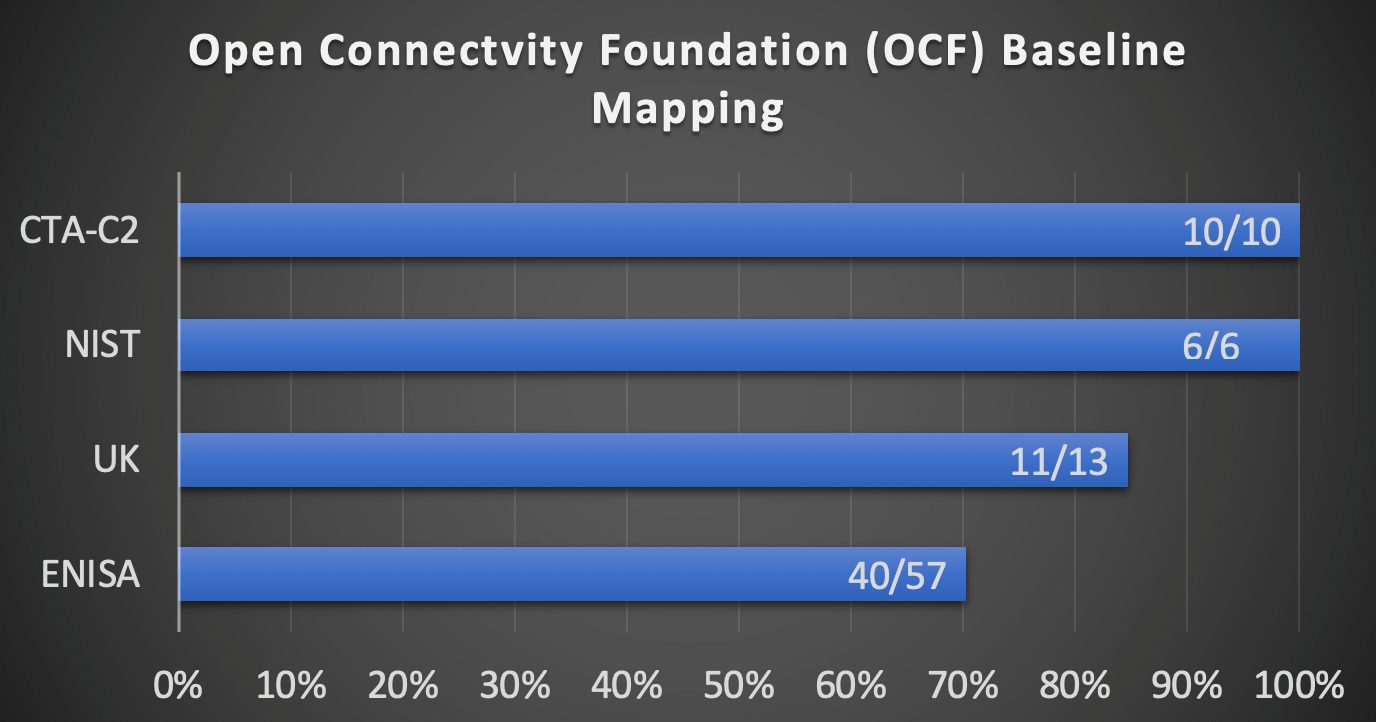
Figure 1: OCF mapping of Security Baselines
The road ahead for 10G and IoT is bright. Ultra-fast networks and connected devices have the potential to change every aspect of daily life, making our surroundings aware and interactive to our presence and able to predict and adjust to our needs. Work, entertainment and social interaction will happen whenever and wherever we are, dynamically and organically. Education and healthcare will be forever changed as sensors and ubiquitous devices allow us to interact in ways never before possible. Yes, the future is bright, but it also must be secure.




