Security
But it’s Just a Light Bulb, Does it Need All This Security?

A version of this blog was published by S&P Global Market Intelligence.
In IoT security, one of the common arguments is about “how much security” a given device needs (as if we could measure that in grams). The typical example is usually a light bulb. The objective in asking the question this way is usually to vacate some or all of the security requirements for that class of device; the real question we care about, however, is the security available to protect the network, not the just the device.

The light bulb question tricks us into thinking in the wrong frame, it focuses on the device and not the network.
- Why would anyone attack this?
- What would they do if they compromised it, turn my light on and off?
If an attacker were able to compromise the light bulb, they may initially try to test the compromise with a change in command from on to off and back again, but then they would likely not do anything else that would signal the fact that they’ve gained control over that device. The likely target was never the light bulb, this is just a means to an end and part of a larger attack vector.
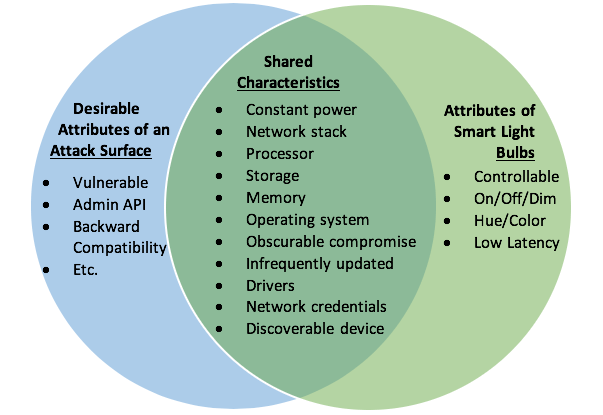
The light bulb is an interesting initial attack target for several reasons. One of the most pertinent aspects is the fact that the bulb has constant power. The light may be off, but the “smart” element of the bulb is awake and listening to network traffic. The bulb also has a network stack, this is how it communicates with the smart light switch, the rules engine, the family hub, or the owner's phone; this bulb isn’t just listening, it’s also transmitting on that network.
To do this work, the bulb also has a processor; since custom hardware is expensive, that processor can likely perform many functions (so that it can be included in other IoT devices) if not address them all generally. The light bulb also has storage for maintaining state, auditing, and communication, memory to run the operating system and the network stack. Additionally, the bulb also includes drivers for the filament, LEDs, coloration, and dimming aspects of the bulb. Most importantly, when we onboard the light bulb into a network that allows us to control the bulb, we provision that device with networking credentials.
The combination of the above aspects of the smart bulb, combined with either the extremely unlikely chance of discovery or the potentially less likely chance that the firmware or operating system will be updated by the user, make this an excellent first attack point for a network. Once compromised, the attacker can cautiously watch the network, potentially interact with other devices on the same network (including cameras and sensors), spoof other devices, and even perform some physical actions that could compromise the safety of the inhabitants of the home (e.g. by advising the front door to unlock or turning the oven on).
It’s unlikely that anyone - other than a prankster or the neighbor whose house you insist on parking in front of - wants to turn your light off and on. That said, the likelihood of other malicious attacks, the ability to gain access to your network and to the other devices in your home make the light bulb a perfect first step in an attack. A well-known cybersecurity attack principle is lateral movement. An adversary compromises a less protected target on a network and then uses that device or system as a pivot point to perform reconnaissance, move laterally in the network, escalate privileges, and finally reach their objectives.
The ability to find devices such as a light bulb and attack them has never been easier; adversaries can use device identification tools (e.g. shodan.io) to find these light bulbs (both online and as a pin on a map) and then attack them. Some of these light bulbs provide discovery and introspection information that may make for easy interactions within the home but also allow attackers to look up specific attacks based on known vulnerabilities in that bulb’s device and firmware version. These attacks are carried out either locally from a radio within the attacker’s car, or from across the globe, if they’re internet-connected.
Once the light bulb is compromised, they can horizontally attack the rest of the network, attempt to escalate privilege, interact with the other devices, and even use other legitimate devices to spoof interactions with outside equipment, other internet connected services, or other bridged devices within the home. Underestimating the importance of the security for all devices leads to holes in network security and is a path to risk exposure (financial, privacy, safety, litigation, and well-being). It’s not just a light bulb, it’s the network, and that network needs to have strong security.
At CableLabs, we are partnering with manufacturers and working to protect consumers and their networks; to do this, we are contributing device security expertise to IoT standards bodies like OCF and to open-source initiatives like IoTivity. Please join us in these initiatives, either as part of the creation and engineering process or by leveraging this work in your devices.




