Security
Adversarial Engineering

Security engineering is one of few technical endeavors in which you deal with an adversary. There are a few other domains such as electronic warfare or fire prevention. Working against an adversary in this way is like playing a twisted game of chess. As the game begins, the security engineer is aware of most of the board and most of the pieces. The attacker discovers the board and pieces as the game is played. Both players invent new rules or change old rules throughout the game without telling the other player. Either player may introduce new squares to the board, new pieces to the game, or remove them. The twisted advantage that the attacker has is that they can use the security engineer’s pieces sometimes.
Security engineering makes for a rough game. The stakes are very high. Revenue loss and brand damage to companies can be huge. Ponemon Institute released a study in June 2016 that indicates the average cost of a data breach is $4 million while the average cost per lost or stolen record is $158. Of course, the actual and incidental damages of each particular breach is unique. The largest security events impact many millions of customers. Information is Beautiful provides a fascinating interactive graphic showing the history of the world’s biggest data breaches since 2004.
All in the mindset
Ultimately, attackers hijack the intended user experience to achieve personal goals — financial gain, extortion, fame, fun, harm. How does the security engineer cope? The security engineer needs to approach work with the mindset of their adversary – the attacker. I like to call this approach adversarial engineering. An adversarial engineer focuses on how to misuse or change a service or product with an eye towards what attackers (various kinds of cyber criminals) may want to do. This way, the adversarial engineer can better integrate mitigations and controls to keep hackers out.
Tools and strategies for adversarial engineering
The adversarial engineer understands and identifies security problems by thinking offensively and creatively about how to get a network or IT resource to provide access to data that shouldn’t be available or provide functionality that isn’t intended. The adversarial engineer employs some great tools and strategies, including:
- Threat analysis — The adversarial engineer creates models of the architecture used to provide services. Hacking techniques can then be postulated on how malcontents might try to access the network, servers, databases, and other resources used to provide services. Threat vectors are identified so they can be can be systematically addressed, ensuring each vector is faced with multiple controls and mitigations to prevent hackers from achieving their goals.
- Misuse cases — Network and IT services are dynamic and fluid, reacting to events and changing state as users interact with resources. Service designers create use cases that define how resources should behave and be used. The adversarial engineer needs to consider these use cases and develop “misuse” cases for each one. Once misuse cases are crafted, multiple controls and mitigations are considered and integrated into the overall solution to foil bad actors from hijacking user experiences and doing unintended activities.
- Vulnerability scanning — Even well designed services can be vulnerable. The adversarial engineer discovers what they may have missed the same way hackers might — they use a variety of tools to scan network interfaces and computer resources for vulnerabilities. Classic examples of such tools are nmap developed by Gordon Lyon, aka Fyodor Vaskovich, Metasploit developed by HD Moore (now available from Rapid7), and Nessus (from Tenable Network Security). There are dozens of other tools available, sometimes packaged into entire environments such as Kali Linux (offered by Offensive Security). Some very advanced scanners look for completely new kinds of vulnerabilities using code analysis or by performing fuzzing.
- Penetration testing — Once vulnerabilities are discovered, the engineer needs to go one more step. They need to find how vulnerabilities might be exploited by doing penetration testing. This is where the craft of adversarial engineering can get deeply technical. Hand crafted investigation is often applied. However, many penetration testing tools are packaged in the same environments as mentioned above under vulnerability scanning.
- Pervasive monitoring — Not all intrusions can be stopped – the Internet, by nature and design, is a fairly open environment. Pervasive monitoring keeps tabs on services and their associated resources, continually watching to ensure that things are being used as expected and performing as designed. This helps to minimize the time intruders are in systems or networks and potentially decrease the damage done by intrusions. Often, hackers will find vulnerabilities that were not discovered by the adversarial engineer and new controls and mitigations will be integrated into the service infrastructure.
Mitigations and controls
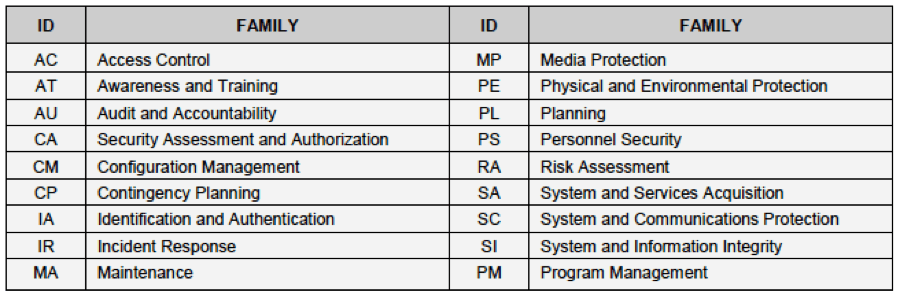
What are the mitigations and controls that adversarial engineers consider? There are literally hundreds. The US government identifies over 300 fundamental controls in the NIST Special Publication 800-53, Security and Privacy Controls for Federal Information Systems and Organizations (“800-53”). There are several families of controls, summarized from 800-53 in the table below. Not all of these are applicable to commercial services, and commercial services often need more than what is applied by the government. A more concise list is maintained by the Center for Internet Security, CIS. These provide a minimum framework for effective cyber defense and are available at the Center for Internet Security website.
Figure 1: NIST 800-53 security control identifiers and family names
Applications must be considered as well. A good starting point is the Open Web Application Security Project (OWASP) who, similar to CIS, maintains a top 10 list as well.
The challenge in applying network and application controls is achieving defense in depth. Achieving a robust security strategy requires deploying controls and mitigations in multiple dimensions — in line, at multiple layers, and even in time. The adversarial engineer assumes controls may be compromised, so they will try to contain or at least slow perpetrators so they can be recognized and stopped.
Pervasive monitoring enables an agile operations strategy referred to as “kill-chains”. This is a “special forces”-inspired approach where you design multiple areas in your strategy where adversaries can be monitored, intercepted, and stopped. The idea was initially documented by Lockheed Martin to proactive detect and respond to persistent threats. Today, this is an increasingly applied strategy to provide an agile response to the ever-evolving tactics and strategies of hackers.
Its not ALL about bad actors
Network equipment fails. Applications do not always behave as designed. Mistakes are made. Sometimes, network attackers will at least partially succeed. Consequently, good networks are actually designed to fail well. The adversarial engineer also considers how resilient the network and security controls must be to achieve design goals. Systems and software will be deployed redundantly, sometimes to extreme levels, so that if something does fail, it doesn’t completely take down services. And, because things do break in the real world, graceful recovery after disruptions and outages must be designed.
What about CableLabs?
CableLabs ensures cable operators have multiple tools to apply adversarial engineering practices. For example,
- DOCSIS® technology includes three areas of control and mitigation: authentication, encryption, and integrity. And, DOCSIS implementations allow for controls both in the network and also at the home or business.
- CableLabs is developing new specifications that also provide for secure devices in the home, including access points, home routers, and even IoT devices.
- CableLabs is developing extremely high speed wireless environments to extend the reach of network operators into communities, cities, and campuses, and security is a core consideration of these emerging technologies.
- CableLabs is considering new ways to secure applications and hardware in virtualized environments and clouds.
Security engineering is challenging given the adversarial nature of the Internet and cable technology is meeting that challenge.