Security
ETSI Security Week: Securing Networks Requires a Global Perspective

Cyber attacks are on the rise and a threat to critical infrastructure around the globe. CableLabs along with other service providers and vendors are collaborating through European Telecommunications Standards Institute (ETSI) to ensure best practices are consistently deployed in regards to these attacks.
Take a look at any cyber attack and consider where the attacks come from and who their victims are. You’ll find that almost all attacks are international in scope, with both attackers and victims found across a transnational field devoid of boundaries. Securing our networks and services requires a global response and our evolving practices and strategies must have an international perspective. CableLabs does this by participating in multiple international organizations working hard to evolve our cyber security defenses. Last week, the ETSI hosted a series of focused workshops on network security at ETSI Security Week. CableLabs helped plan this event, and we contributed our insights in presentations and panels.
This annual event is attended by nearly 300 industry professionals and opens a dialogue to develop a common understanding in the industry of best practices. Workshops included public policy impacts on security practices, Machine to Machine/Internet of Things security challenges, securing Network Function Virtualization (NFV) architectures, and, no event is complete without some discussion of 5G. (For more information on 5G see Tetsuya Nakamura’s blog post here.) I presented our experiences in implementing NFV proof-of-concepts and Brian Scriber participated in a panel discussing operator perspectives. Materials shared at the event are available after registration on the ETSI portal here.
As shared here last fall, as well as introducing new security challenges, NFV also presents opportunities to improve the security of future networks relative to legacy infrastructure. Benefits of a well implemented NFV infrastructure enables:
- More consistent security processes and controls
- Easier and more rapid security upgrades and patching as threats evolve
- Improved support for pervasive encryption
- More cost-effective security and performance monitoring
With the correct implementation, NFV enhances security operations by enabling pervasive monitoring and more agile and flexible responses as cyber threats evolve.
NFV coupled with Software Defined Networking (SDN) enables the creation of an open and distributed architecture which enables operators to create “network factories”. Network factories are fully automated network architectures that are entire supply chains for exciting new services. We need to secure the network infrastructure, as well as secure the software supply chain from code creation to delivery as running code on the platform. This requires a different orientation from today’s operations. Fortunately, NIST has provided a framework for approaching the cyber security aspects of supply chains and it applies well to open and distributed architectures.
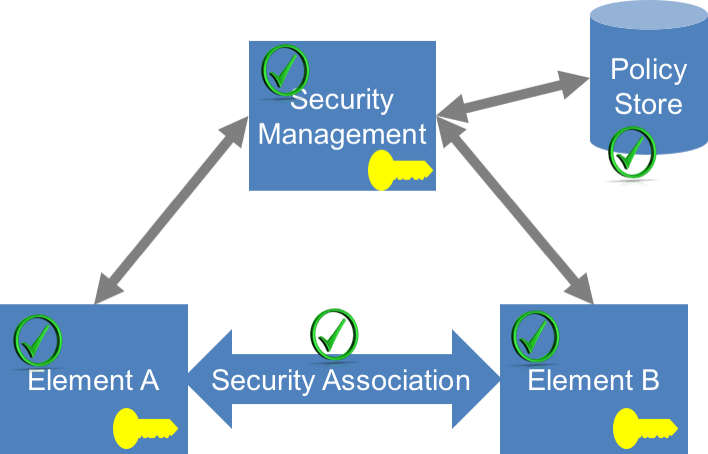
ETSI is a leader in providing foundational standards for NFV and is the single most influential body on NFV security best practices today. The ETSI NFV Architectural Framework sets the stage for what most other standards bodies and open source code projects are attempting to achieve. ETSI’s NFV reference architecture does not currently adequately identify all the supply chain cyber security aspects. Consequently, we haven’t yet defined a comprehensive approach to establishing security associations between all of the components (which may be hardware or software).
Every connection in the network should be considered as a security association. Certain security functions must be implemented for each security association. Each security association should be:
- Based on strong identity: This means there needs to be a persistent private key associated with a unique identifier and attested (signed) by a certificate or equivalent
- Authenticated: Using some form of cryptographic challenge
- Authorized: For both network and process access control and based on a network-wide policy
- Isolated: From other sub-networks and workloads on virtualized servers
- Confidential: Including encryption
- Attested: The infrastructure and communications links are proven to be untampered
Providing a basis for strong identity is proving to be challenging. CableLabs has used PKI-based certificates for strong identity for DOCSIS network now for 17 years with over 500M certificates issued. Yet, achieving consensus to replicate this success amongst the evolving solutions in NFV, IoT, and medical devices are taking time.
Security identity requires three components:
- The first element is a secret, which is usually a private key to support authentication and encryption.
- The second element is a unique identifier within the ecosystem. DOCSIS network security uses the MAC address for this purpose, but that is not applicable to all other domains.
- Thirdly, the identity must be attestable. This means creating a certificate or profile that is signed, which binds the certificate to the secret.
The path to success in implementing globally effective cyber security is to document best practices through specification or standardization with supporting code bases which actually implement those practices. CableLabs is proud to be a major contributor to ETSI’s NFV project. We lead both the ETSI NFV Operator Council and the Security Working Group and we are collaborating with other industry leaders to address these gaps. Further, we work closely with open source code groups such as OpenStack, OSM, OpenDaylight, OPNFV, and we watch emerging initiatives such as FD.io and ONAP. Through our SNAPSTM initiative, we are reinforcing standards work with practical experience. If these initiatives mature, we will adapt the practices to cable specific solutions.
--
CableLabs is hosting the next ETSI NFV plenary meeting in Denver,CO from September 11-15, 2017. Participation is open upon signing the ETSI NFV participant agreement. Leave a comment below if you’d like to connect with the CableLabs team. We’d love to meet you there!